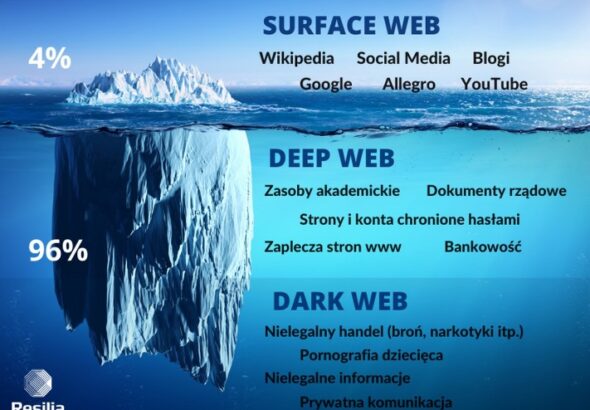
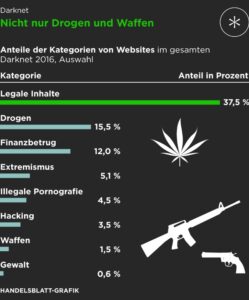
For sellers, it’s often about making money while staying off the radar. As a user or cybersecurity...
Exclusive Monero usage signals a heightened prioritisation of anonymity. Once they identify it, they can break into...
Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple...
Vice City’s 700+ vendors focus heavily on drugs (80% of its 18,000+ listings), rated 4.6/5 across 25,000+...
The dark web markets and the darknet vendor shops have the tendency to cause exit scam which is fleeing away with...
We extended our analysis this year from three to five of the biggest black markets on the...
You can even find things such as BIN checkers and PayPal cookie converters. Another reason the Russian...
As was the case on Reddit, there are subs entitled /d/darknetmarkets and /d/darknetmarketsnoobs on Dread. Darknet market...
Impreza provides an affordable hidden space for black websites to base their operations. Impreza rents servers, registers...
Simply complete a Bitcoin address search to view it on the blockchain. Plus, visit our Bitcoin Charts...