Web inventory tool that captures screenshots of webpages and includes additional features for enhanced usability. Automate your reconnaissance process with AttackSurfaceMapper, a tool for mapping and analyzing network attack surfaces. The moment has arrived – the DEF CON 33 Call Season is officially afoot! Whether you’ve got ideas to start a new Village, or have the tunes to rock the crowd after hours, the doors are open. There are a bunch of Calls you can peruse at leisure from Contests to Soundtrack to Vendors, and all the info you need to get started is on the DEF CON 33 Call Index.
Trend Micro Warns Of Apex One Zero-day Exploited In Attacks
EDB published dozens of exploits after this date, so any 2023-specific statistics might look wrong, but the reality is they were largely silent until late March. The tradeoff is you necessarily need to smooth traffic bursts out to meet the fixed rate and that introduces high latency. Unfortunately most user traffic is bursty and not continuous. For real anonymity you need something that scrambles and delays your traffic to make it harder to track. Something that breaks big transfers up into a bunch of small transfers, sends them via different routes, and generally makes your experience miserably slow. When you’re evaluating any security product you always have to determine if the security properties the tool provides match up with the security properties you need.
ProPublica — Investigative Journalism On Tor
This information is for informative, educational and research purpose only. This information can be used for intelligence gathering for your incident investigations and for the purpose of securing your organization. The motive of providing this information is to share intelligence and secure organizations from cyber threats.
- 0-days are special because your target has no idea such a vulnerability even exists.
- Dive into a seed catalog and you’ll see that there are nearly as many onion varieties as there are tomato varieties.
- ProPublica is a non-profit investigative journalism outfit based out of New York City.
- Now that you understand a bit more about short-day and long-day onions, here are a few of our favorite varieties.
- Exploit code was publicly disclosed as well before Mozilla released the patch.
Local offices frequently monitor suspicious activities that involve their jurisdictions, so authorities might be closer to your anonymous communication than you know. Insights like these help researchers and advocates understand how and why Tor is being used. With this info, the wider online community can grasp Tor’s impact and its ability to provide secure and anonymous internet access. Null Byte is a white hat hacker world for anyone interested in hacking, science, networking, social engineering, security, pen-testing, getting root, zero days, etc. This heirloom long-day onion is famous for its large and sweet bulbs characterized by a golden hue.
Navigating the dark web is like starting an epic quest — it’s dangerous to go alone. Contributions are welcome, but ensure they align with ethical use. If you encounter issues, please report them on the GitHub repository. A GitHub application that performs automated security code reviews by analyzing contextual security aspects of code changes during pull requests. Fractional CISO service that helps B2B companies implement security leadership to win enterprise deals, achieve compliance, and develop strategic security programs. A LinkedIn reconnaissance tool for gathering information about companies and individuals on the platform.
Further Reading
This means you only have to worry about a few of these happening at a time, which makes it easier to detect (pull on one thread, and the rest start to unravel). Or if you know your image manipulation library has tons of vulnerabilities, you could run it in a locked-down sandboxed environment where exploitation doesn’t get the attacker much of anything. Visiting onion sites on older Tor versions can needlessly expose you to added risks. Since most Tor websites are non-indexed and unregulated, the probability of scams is much greater on the dark web.
New CrushFTP Zero-day Exploited In Attacks To Hijack Servers
Do not utilize this information for illegal, unauthorized, and unlawful activities. We read every piece of feedback, and take your input very seriously. In 2024, Operation Cronos, a global law enforcement initiative, successfully took down 34 of LockBit’s servers and seized decryption keys, stolen data, and cryptocurrency wallets. While LockBit managed to rebuild its infrastructure, this new breach highlights the fragility of its resurrection. Apple’s iOS 26 and iPadOS 26 updates are packed with new features, and you can try them before almost everyone else. First, check Gadget Hacks’ list of supported iPhone and iPad models, then follow the step-by-step guide to install the iOS/iPadOS 26 beta — no paid developer account required.
Microsoft August 2025 Patch Tuesday Fixes One Zero-day, 107 Flaws
“Completely avoid the scam/scum and enjoy real code, real information and real products.” In 2022, 0day.today published 943 exploits, and EDB only managed 401. In fact, we were surprised to find that 0day.today has published more exploits per year than EDB since 2012 (with the exception of 2019).
Comment 7
So add ignoring security guidance to the list above, and, well, I’m suspicious. Everything I needed to understand what was going on with “Spring4Shell” – translated source materials, exploit, links to demo apps, and more. The Tor Rendezvous Specification v3 specifies a new address format. Instead of the quite short v2 Tor addresses which were based on RSA, the new v3 format will have 56 characters and ed25519 elliptic curve keys. The trick is akin to living on a street with a unique name and a retailer auto completing your address and customer details because you’ve ordered from them before and you gave them your street name. It was years later that a “0day” went from a copy protection removal/crack (“0day warez”) to its more general modern usage in computer security.

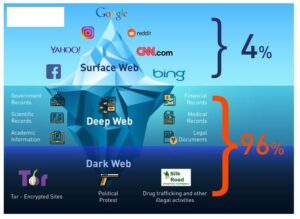
Access The Dark Web Anonymously & Securely
A VPN like Surfshark encrypts your internet connection and makes it harder for others to see your real IP address. This adds another, more reliable security layer to all of your online activity. SecureDrop has even been adopted by various news organizations worldwide. It provides a safe haven for anyone looking to shed light on wrongdoing or share critical information with the media. SecureDrop is designed explicitly for journalists trying to preserve the privacy of their sources. Its anonymous nature enables users to create and submit encrypted documents, chat securely, and receive private responses from journalists.
Cut into a Red Stockton onion and you’ll be met with concentric pink and white rings. The thick-skinned bulbs have an excellent storage life and are quite flavorful raw or cooked. The large, flattened bulbs have a crisp texture that only gets better with cooking. Vidalia onions are Yellow Granex onions that were grown in the low-sulfur soils of Vidalia, Georgia.
DEF CON 33 is winding down now, and we want to take a moment to thank the whole DEF CON community for another amazing year. Thank you for bringing your boundless energy and curiosity to this little party we throw. Thank you for spending another long enchanted weekend teaching each other, learning from each other, and partying with each other.
Some readers may be looking to explore recent OS-specific vulnerabilities — or simply trying to remain aware to better protect themselves. Most operating system distributions offer an advisory listing on their website. These are mostly application-specific vulnerabilities and bugs, but in many cases, can be easily exploited by attackers. CVEs and exploits are highly sought after by black hats and security professionals alike. They can be used to hack into outdated Windows versions, perform privilege escalation, and access routers without the target’s knowledge, among other things. Tom joined LADbible Group in 2024, currently working as SEO Lead across all brands including LADbible, UNILAD, SPORTbible, Tyla, UNILAD Tech, and GAMINGbible.
It’s committed to transparency and public service, which is why it maintains a dark website along with its site on the surface web. Not to be confused with the riskier Hidden Wiki page, Wikipedia on Tor serves as a vast repository of information. You’ll find articles on a wide range of topics, such as history, science, and culture — and that’s just scratching the surface. So take this guide as you explore where to go on the Tor Browser without risking your online security. As a gesture of goodwill and to assist those affected by our previous activities, we are offering free decryption software to all companies that have beenimpacted by our ransomware. Our goal is to ensure that you can recover your encrypted data without the burden of paying ransoms.
The breach comes just months after law enforcement’s Operation Cronos attempted to dismantle LockBit’s infrastructure. The Computer Incident Response Center Luxembourg (CIRCL) is an information security organization designed to handle cyber threat detections and incidents. Its website features security research publications and a searchable CVE database. This Italian heirloom is as beautiful as it is delicious.