Understanding this ecosystem underscores the importance of proactive cybersecurity risk management to prevent business and personal data from entering the underground market. Employees with legitimate access to business data can pose an internal risk, either by intentionally selling sensitive information or unknowingly exposing data through negligence. A 2023 report by IBM found that insider threats account for nearly 20% of security incidents, highlighting the need for strict access controls and monitoring. Cryptocurrency exchanges are online platforms where individuals can buy, sell, and trade various cryptocurrencies. These exchanges provide the necessary infrastructure for converting digital currencies into fiat currencies and vice versa.
Good Password Ideas And Tips For Secure Accounts
- You may encounter artificial intelligence being employed to analyze user behavior, potentially increasing the risk of exploitation for unsuspecting users.
- Cash on Delivery (COD), the age-old payment method that has stood the test of time, remains a popular choice for consumers, particularly in regions where online shopping is on the rise.
- As awareness of cyber threats grows, governments and industry bodies are likely to introduce stricter regulations surrounding dark web monitoring and data protection.
- The dark web’s association with bitcoin has created a negative image in the eyes of some, with concerns about its potential for illegal activities and lack of regulation.
- Regularly review the marketplace’s guidelines and stay updated on any changes or new security measures.
Chip and PIN technology became standard in the 2010s to make physical card cloning more difficult, forcing carders to rely more on online methods. E-commerce platforms began implementing machine learning and AI-based fraud detection systems to identify suspicious patterns and transactions. CAPTCHAs and multi-factor authentication were introduced to prevent automated bots from exploiting online systems. The dark web supports anonymous transactions that are challenging for law enforcement to trace or disrupt.
Awazon Market Link And Access Guide 2025
In this article, we will guide you through the process of selling on the dark web and share some tips and precautions to ensure a successful and secure experience. Businesses must implement robust security measures to prevent data breaches and mitigate cyber risks. Conducting regular cybersecurity risk assessments helps identify vulnerabilities before they can be exploited. Assessments should include penetration testing, vulnerability scans, and compliance checks to ensure adherence to cybersecurity regulations. On one hand, increased regulation and scrutiny may deter individuals from engaging in illegal activities, ultimately making the dark web a safer place.
What Are Dark Web Bitcoin Mixers?
- Additionally, the anonymity provided by cryptocurrencies ensures that the identities of the parties involved remain hidden, reducing the risk of detection by law enforcement agencies.
- One of the primary reasons why Bitcoin became popular on the dark web is its inherent nature of allowing users to transact without revealing their identities.
- Credit muling networks thrive on the Dark Web, connecting individuals willing to act as “mules” with criminal organizations seeking to launder money or carry out fraudulent activities.
- PayPal is widely used by online merchants and even real-life stores, allowing you to make private purchases from almost anywhere.
- Law enforcement agencies face significant challenges in combating these networks due to the complexities of the dark web.
Education and awareness about the legitimate uses of Bitcoin are key to combating the negative perception created by its association with the dark web. Additionally, Bitcoin transactions can be linked to real-world identities through various methods, such as analyzing transaction patterns or tracing IP addresses. Despite its association with the dark web, it is important to note that bitcoin itself is not inherently illegal.
Data Encryption & Access Controls
You need to give PayPal a lot of personal information when you create your account, including your email, phone number, and even a government ID. However, the e-wallet company still knows your identity, as they collect your data behind the scenes for security and regulatory purposes. Security solutions like anti-virus software protect your system and network from malware and other threats. The dark web, being a hub for criminal activities like identity theft and malware distribution, exposes you to various security threats like malware or phishing.
In the event that either party is dissatisfied with the escrow service’s decision, they may explore other legal avenues available. However, it’s important to understand that on the Dark Web, traditional legal recourse may be limited or nonexistent due to the anonymous and unregulated nature of the platform. Therefore, relying on escrow services for dispute resolution is typically the most practical approach.
ECommerce Fraud: How Fraudsters Use The Dark Web To ‘Warm Up The Shop’ And Fool Rules-Based Anti-Fraud Systems

The fees vary depending on the payment method you choose and the size of your transaction. It’s important to understand these fees before you start trading, so you can factor them into your decision-making process. When it comes to trading cryptocurrencies on GDAX, setting up your payment method is an essential step. It’s important to ensure that you have a reliable payment method in place to make purchasing and selling digital assets as seamless as possible. This section will provide you with insights on how to set up your payment method on GDAX, and what to consider when choosing the right payment method for you.
Inside The Exploit: How Your ChatGPT’s Uploaded Files Could Be Stolen By Prompt Injection Vulnerability
Bitcoin’s digital nature, combined with its decentralized nature, made it an ideal currency for these transactions. Bitcoin mining, a crucial process for validating and recording transactions on the digital currency’s decentralized blockchain, requires significant computational power. As the popularity of cryptocurrency has surged in recent years, so has the demand for mining equipment and energy. However, some individuals and organizations have found a way to exploit the dark web’s anonymity and privacy features to engage in illicit mining activities.
Businesses must navigate these complexities carefully, ensuring compliance with regulations while protecting their interests. Now, let’s move on to discussing important safety measures to consider when using escrow on the Dark Web.
The anonymity offered by online forums and chatrooms on the dark web plays a significant role in facilitating credit muling networks. Participants can create pseudonymous accounts, making it difficult for law enforcement agencies to track their activities. Additionally, the dark web’s encrypted communication channels provide an added layer of security, ensuring that discussions and transactions remain hidden from prying eyes.

It only displays your username during the transaction, and though you’ll need to verify a card, you can use a virtual card when signing up. If you need something totally private, I’d recommend gift cards or prepaid debit cards instead. For example, most “anonymous” apps only use pseudonyms, so the merchant can’t see your details, but the company itself still collects your data. Sophisticated methods like live admin panels and payment cloaking make scams harder to detect.
NFC-enabled POS Terminals – For Sale On The Dark Web
Credit card details sell for $5 to $120, while a hacked corporate database can be worth thousands of dollars. According to cybersecurity research firm Digital Shadows, over 15 billion stolen credentials are actively traded on Dark Web forums, driving an underground economy worth billions of dollars annually. Protecting your personal information is vital when it comes to guarding against credit card fraud on the Dark Web.
How A PayPal Account Or Credit Card Ends Up On The Dark Web
For frequent, anonymous transactions, a privacy-focused hot wallet (like Electrum or Wasabi) combined with a cold wallet for storing large balances is ideal. The Tor Browser is specifically designed to protect your anonymity by routing your traffic through multiple servers, hiding your IP address and browsing history. A Virtual Private Network (VPN) encrypts your internet connection and masks your IP address, providing a crucial layer of anonymity. While SSN, name, and DOB are all fairly standard in fullz, other information can be included or excluded and thereby change the price.
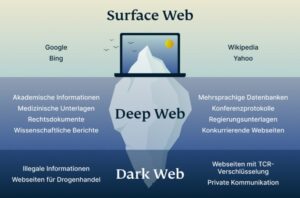
The dark web contains a range of content, some of which is illegal, including marketplaces for drugs, weapons, stolen data, and other illicit services. The use of cryptocurrency on the dark web offers convenience, trust, and anonymity to buyers and sellers. The adoption of privacy coins like Monero is increasing due to their non-traceability and lower transaction fees.