
So that is another page for every page that is on the live site. Meanwhile our company intranet is hidden from search engines, and requires a password. You can browse to it if you know the URL, but it won’t appear in a Google search.
How To Access The Dark Web Safely: Step-By-Step

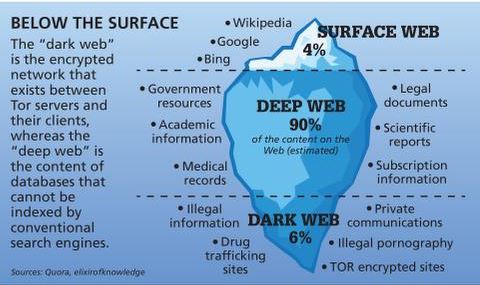
The websites you visit every day aren’t all there is to see on the internet — not even close. Beyond this “surface web” is the deep web, and within the deep web is the dark web. Then, use data breach monitoring software to help find out if your personal data has leaked onto the dark web. While accessing the dark web isn’t necessarily wrong or illegal, it’s important to know how to navigate this part of the internet safely. Accessing the dark web isn’t like surfing the web everywhere else online.
So don’t be surprised if you encounter different versions that claim to be genuine, and be very careful. Purchases through links on our pages may yield affiliate revenue for us. We review and list tools and products without bias, regardless of potential commissions. A VPN can help disguise your use of Tor and your visits to dark web resources. If you need to access dark web resources, these are the steps you need to take.
Can You Be Tracked If You Use Tor With A VPN?

There are both free and paid VPN services, but if you’re planning on accessing the dark web, you’re going to want to opt for a high-quality paid VPN that offers you plenty of protection. The difference between the surface web and the deep web is that pages, websites, and content on the deep web are only accessible to authorized users with the appropriate credentials. In other words, these are pages that aren’t indexed and therefore can’t be found by a typical search engine. I2P is an anonymous overlay network that can only be used to access hidden websites and services that are unique to the I2P network.
WANT TO TRY THE TOP VPN RISK FREE?
The .onion site has thousands of downloadable comic books ranging from niche to mainstream. As with the Imperial Library, you should be aware of copyright infringement. Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol. It assigns a task to the client instead of the server, eliminating server-related vulnerability.
How To Access The Dark Web Safely Step-by-Step In 2024
Instead, you often have to consult directories to find lists of legitimate sites and visit and access them that way or use special dark web-friendly search engines. Many cybersecurity and tech experts recommend using a VPN whenever you want to access the dark web via the Tor Browser or any other specialist browser. A quality VPN like ExpressVPN will encrypt your internet traffic and mask your IP address, providing an extra layer of anonymity when establishing the initial Tor connection. This guide explores how to access the dark web safely on different devices while also covering both the benefits and risks of delving into this part of the internet.
- Put simply, the deep web is all the information stored online that isn’t indexed by search engines.
- Being hidden doesn’t translate into being completely protected from the possibility of tracking, or, when it comes to illegal activities, of risk.
- The dark web is known to host illegal and disturbing types of pornography, including child exploitation and violent content.
- The following sections will explain how to access the dark web on different devices.
- Thankfully, it allows you to connect unlimited devices, which will be useful when exploring the onion links with many devices.
Exiting Safely
Accessing the dark web requires special tools and precautions, like using the Tor browser. However, the Tor network can be hacked, as evidenced by the 7 months of DDOS attacks experienced in 2022 (Securityaffairs)1. You might also consider using virtual machines (VMs) for an added layer of security.
What Are The Best VPNs To Access The Dark Web With Tor?
Its VPN Accelerator distributes the CPU load between multiple processes in OpenVPN, and modifies the servers’ Linux stacks to shorten the normal packet processing path. All Surfshark servers are RAM-only and support the WireGuard, IKEv2, and OpenVPN protocols. The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a SHA512 authentication hash and 2048-bit DHE-RSA key exchange. While NordVPN is undoubtedly a great service, it’s not without fault. In 2018, someone gained access to a third-party data center in Finland. NordVPN responded aggressively by upgrading its entire infrastructure to RAM-only servers and ending its reliance on rented servers.
A VPN service helps you remain secure and anonymous by encrypting your data and masking your network address. This prevents cyber criminals prowling the dark web from snooping on your activity. Therefore, to access the deep web, you need passwords to those databases.
If you’re intrigued and want a firsthand experience, follow this guide to learn how to access the deep web with an anonymizing browser. We’ll use the Tor browser for this guide, but any other browser that supports the Tor protocol will do. Cloudwards.net may earn a small commission from some purchases made through our site.
Tor And Onion Routing Explained
These features are accessible from the Freenet interface under the “Community” and “Tools” sections. You can enter .onion URLs directly into the Tor Browser’s address bar or visit directories like The Hidden Wiki to find popular sites on the dark web. Another challenge of finding dark web sites is that they don’t often last long. Many sites become defunct quickly, either because they are shut down due to illegal activity, their founders lose interest, or they change addresses and names to avoid detection.
FAQs About Accessing The Dark Web Safely On Your Phone
Tor is the most popular way to access the dark web, but it’s not the only option. Other privacy networks like I2P, Lokinet, and Freenet offer different layers of security and anonymity. Each tool works differently, and some are better suited for specific use cases than others. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails. This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to.



