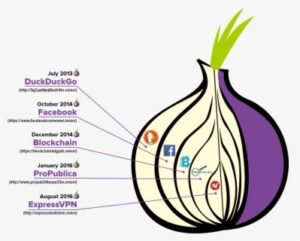
Being the unregulated part of the internet, the dark web is full of illegal activities. The chances of opening websites with malicious, inappropriate, or illegal content are very high, especially if you don’t know the exact .onion website you wish to visit. Traditional social media platforms such as Facebook have also created versions that work with the dark web to provide services across all dimensions of the World Wide Web. However, unlike Facebook, the DWSN requires users to remain anonymous and not reveal personal information to protect privacy. There is a significant risk that the government can target you for visiting a dark website, as many Tor-based sites have been taken over by police authorities worldwide.

Hidden Facebook is hardly the only social media client on the dark web. People mostly use it for covert communication, anonymous tips submission, and stuff like that. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations. The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily.
However, note that Dark.fail monitors site uptime status and cannot tell whether the site is safe. To stay safe and private when visiting any listed sites, ensure you have a VPN and anti-malware installed and enabled. Riseup is a dark web platform that offers secure messaging solutions. It does not store logs and is protected from interference and malicious attacks. The platform is free and is run by volunteers in the US who prefer privacy and security. The platform utilizes end-to-end encryption, ensuring it does not store any activity records.
Kingdom Market has emerged as one of the most enigmatic dark web markets. Its reputation for exclusivity and sophisticated encryption has intrigued security professionals worldwide. Hidden behind layers of anonymity, Kingdom Market has become a hub for illegal trades, from drugs to sensitive data.
Tor2door Market

Chill, because nobody will ever find a record of you ever fiddling around the darknet. Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive. All you’ll need is an 8GB thumb drive, an installation package, and a couple of minutes to get things up and running.
Protection Methods
Torch is funded primarily through advertising—purchased in BTC, of course—which is why you’ll find the front page blanketed with old-school banner ads of dubious origins. Search engines on the dark web are a bit of a contradiction because dark web sites by definition are not indexed by traditional search engines. Your real information could be exposed at these nodes, allowing third parties to intercept your dark web activity.
Tether Announces Plan To Bring USD₮ To RGB, Advancing Native Stablecoins On Bitcoin And Lightning
Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network.
RussianMarket specializes in the sale of “logs”, CVVs, dumps and RDP access. Including everything from drugs, arms, and counterfeit goods, to malware and exploits, and everything in between. This early detection allows organizations to identify and respond to threats quickly, reducing the chances of unauthorized access, financial loss, or damage to brand reputation.
The Hidden Wiki — Collection Of Popular Dark Web Links
But shutdowns like this have become a recurring feature of the dark web. If you have to email a message or files to a vendor, secure your communication with PGP (Pretty Good Privacy) encryption. This makes sure your messages are encrypted and only readable by the recipient. • Get to know the terminology of the marketplace, rules and seller reputation scores.
OnionName — Buy Readable Onion Domains
Once you have accessed the dark web, you can search for and purchase items, engage in activities or participate in underground markets. Understanding its role in facilitating online shopping fraud is the first step in protecting yourself. The seller will check their account and, when they see the funds, release the bitcoin that’s locked in the escrow wallet. Click ‘Wallet’ at the top of the page and you’ll see the BTC in your Localcryptos wallet.

In addition, its technology is open-source, and it doesn’t keep your data, which proves it is safe to use. Keybase is a dark web messaging application that functions much like Signal and WhatsApp, except it is secure and private. This service lets you create your unique domain name with the letters or words you prefer. It has a vast library of over 1.5 billion indexed pages that lets you find whatever you are looking for.
Is The Dark Web Illegal?
For small and medium-sized enterprises (SMEs), the consequences of compromised credentials, data breaches, and reputational harm can be devastating. Addressing these risks requires a proactive approach that combines technology, education, and strategic planning. Businesses face substantial cybersecurity risks due to the proliferation of these marketplaces. Data breaches often lead to sensitive corporate information appearing on the dark web, which can fuel further attacks.
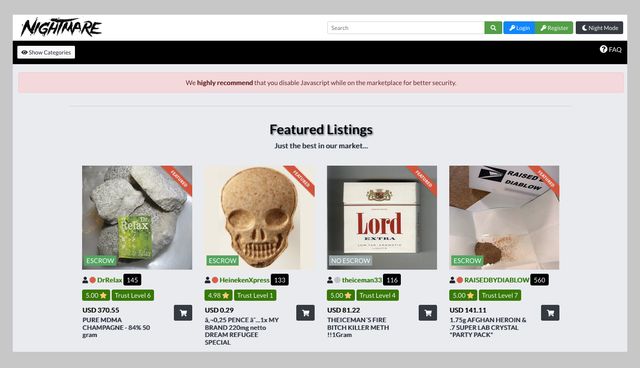
However, the threat of clicking on the wrong link always remains, so be cautious while you use it. To provide freedom of speech and keep journalism a strong pillar of the economy, the BBC made this Tor mirror. It helps people anonymously use the BBC website without restrictions. This includes rare electronics, experimental devices, and high-end hardware. Some sellers offer custom-built gadgets that cater to specific needs. The dark web exists inside layered proxy networks, known as darknets.
Vorm Web Search Engine
- Stolen data can quickly transition from legitimate systems to underground forums, where it becomes a valuable commodity for cybercriminals.
- Tor browsers create encrypted entry points and pathways for the user, so dark web activity remains anonymous.
- This underground economy ranks as the world’s third largest and poses a significant threat to businesses, requiring constant attention from IT professionals.
- On the other, it requires vigilance and responsibility to avoid legal and cyber security traps.
It was suspected as an exit scam; however, a few days after it had gone offline, it was revealed that AlphaBay had been seized and alpha02, aka Alexander Cazes, was caught. Ultimately, this disruption to accessibility is not a unique event. In fact, it is routine for individuals participating in these dark web communities, par for the course of engaging in the markets.
Dark Web Marketplaces: How Illegal Goods Are Bought And Sold

Therefore, it is crucial to stay within the boundaries of the law and prioritize ethical conduct. Protecting your security and privacy should always be a top priority. Use secure operating systems, encrypt your communications, and secure your devices. Utilize tools like the Tor browser, VPNs, and encrypted messaging services to maintain anonymity. By following these steps, you can better protect your identity and maintain anonymity while exploring the Dark Web. However, it is important to note that no method is foolproof, and it is essential to exercise caution and be mindful of the risks involved at all times.