Users of Altenen share techniques and tools for cracking, hacking, and committing fraud. Despite its focus on illegal activities, Altenen attracts a loyal following, with many users seeking to learn the latest methods for committing financial crimes. Also, criminals are increasingly using databases of stolen employee mobile phone numbers to attack employer networks. If your personal information is stolen, monitor your credit report for unauthorized activity or accounts. You can also freeze your credit report for a year after you have been a victim of a data breach. This ensures credit reporting agencies will not provide your credit report if anyone tries to open a new loan or credit card account in your name.6.
But onion sites can also serve nobler goals, like providing access to information and independent journalism in countries with government censorship. Founded by security researcher Juha Nurmi, Ahmia is essentially a list of “hidden” sites that do want to be found. Onion sites are “crawled” and added to the list provided their “robots.txt” file permits it, and if it is not on their blacklist of sites with abuse material. The risk of being a visitor to this content could lead to being placed on a watchlist or immediate targeting for a jail sentence.
How To Delete Yahoo Account In 2025
In conclusion, the darknet continues to evolve, providing a secure and efficient platform for drug trade. By 2025, markets like PhantomX, NebulaTrade, and EclipseMarket are expected to dominate, offering users a combination of privacy, reliability, and variety. Looking ahead, the darknet drug trade is expected to grow further, driven by advancements in blockchain technology and increased adoption of privacy-focused cryptocurrencies like Monero. These developments will likely enhance transaction security and reduce traceability, making darknet markets even more appealing to users worldwide.
Learn Carding Online
By monitoring dark web markets, we often discover data breaches before they’re publicly reported. These systems can often identify when stolen card data is being tested before major fraud attempts begin. Banks and credit card companies lose billions annually to fraud, but the real cost isn’t just in fraudulent transactions. The impact of dark web credit card fraud extends far beyond individual card holders.
Its strength lies in regular updates and community-driven verification of links. I especially like how TorLinks categorizes links based on their type, letting you easily find what you need. While its name may indicate danger, the dark web can actually be a safe place. It provides safety and anonymity for journalists, privacy-conscious users, or those in high-censorship countries. You need to ensure you’re only accessing reliable dark web sites, and the ones listed below are among the safest ones that currently work. This ensures minimal resource demands and allows for easy implementation within your existing security infrastructure.
How Cryptocurrencies Enable Safe Trade On The Darknet

The term darknet carding sites refers to illegal online platforms where individuals can buy and sell stolen credit card information. These sites operate within the depths of the internet, accessible only through specific software that anonymizes users’ identities. The term darknet carding sites refers to a specific segment of the dark web where illegal transactions involving stolen credit card information take place. These sites offer a marketplace for cybercriminals to buy and sell sensitive financial data, often leading to significant financial losses for individuals and businesses.
What Measures Can Individuals Take To Protect Themselves From Carding?
Besides payment data, threat actors are also monetizing stolen Personal Identifiable Information (PII). Spanish law enforcement dismantled a Brazil‑linked criminal network for carding fraud across 17 provinces. Operating under Operation ALBATROS‑SAMBA, they exploited stolen billing data via phishing and vishing, created virtual cards, and ran fraudulent purchases resold through social media. While consumers face identity theft risks, businesses bear the brunt of financial and operational damage caused by carding.
Deep Web Radio

Inform your bank or credit card issuer immediately to freeze your accounts and prevent further unauthorized transactions. Automated bots are used to test multiple credit card numbers on different websites simultaneously, identifying valid ones for fraudulent purchases. When Torrez closed in December it was one of the largest English-language marketplaces in the world selling drugs, hacking tools, counterfeit cash and criminal services. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info.
The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. Unlike other search engines, it does not collect or share web activities and personal data of users. In the worst cases, they can even use the information they’ve gathered to steal someone’s identity, open an account in that name, launder money, or attempt an account takeover.
It made around $4.1 million since its establishment in October 2017 according to Elliptic’s internal data. The site was infamous for using the image of former US President Donald Trump for its branding. Adjust privacy settings on your online accounts to control who can access your personal information. Limit the personal information you share on social media or other online platforms. Max has 20 years of experience in fraud prevention and financial crime prevention for the US Government and major financial institutions.
- Protect your devices with strong passwords and encryption to prevent unauthorized access.
- Silk Road was one of the most notorious marketplaces on the Dark Web, founded by Ross Ulbricht (aka Dread Pirate Roberts) in 2011.
- The categories are well organized, ranging from drugs and fraud to digital products, guides, and malware.What really sets it apart is its focus on security and usability.
- Riseup is a volunteer-run social movement organization that offers email, email lists, a VPN, online chat, and other online services for political activists engaged in various causes.
- Note that connections inside of the Tor network are end-to-end encrypted by default, meaning there is no separate encryption layer necessary as with regular websites.
- While some of these markets were shuttered by law enforcement agencies – some took the easy way out with exit scams.
Earlier this year, a New York man pled guilty to managing a credit card theft scheme responsible for stealing $1,500,000 from 4,000 account holders between 2015 and 2018. According to the United States Attorney’s Office, the ring of thieves obtained the credit card information on the dark web, and used that information to create their own cards. The fraudulent credit cards were used to purchase gift cards, flights, hotels stays, and other goods and services.
New Shamos Malware On Mac: Beware Of ClickFix Attacks
The timely exchange of this information can help banks better detect threat actors exploiting VCC accounts for money laundering and other fraudulent purposes. The scope of cybercriminal lookup services is not limited exclusively to PII data based on ID, DL or SSN. For example, “NZI Lookup” enables fraudsters to extract banking statements. Bank statements can help threat actors simulate a victim’s established financial behavior, before committing actual theft.
- Despite how big the dark web forum market is, or how many people it attracts, these forums remain a risk to both individual users and businesses.
- Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data.
- If you ever decide to explore the dark web, protecting your identity is crucial.
- In 2025, the landscape of darknet markets continues to evolve, offering users enhanced security, reliability, and accessibility for drug trade.
Eight months after Joker’s Stash went caput, White House Market (WHM), a darknet marketplace, shut down. Then in November 2021, Cannazon, the largest marketplace for buying marijuana-based products, shut after a DDoS attack. Then to round off the year, ToRReZ Market, a site selling illegal products, closed in December 2021. A VPN protects your connection against everyone, not just your ISP and the authorities. It encrypts your connection to prevent outsiders from being able to read your data and masks your IP address with one from a VPN server—so whoever’s looking can’t get any useful information. This process also prevents your ISP from seeing your data or where it’s going.
Curious About How Breachsense Can Help Your Organization Detect Credit Card Fraud? Book A Demo To Learn More
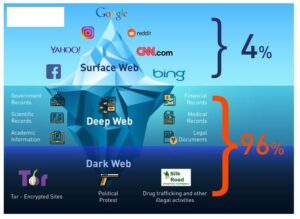
Dark web websites look pretty much like any other site, but there are important differences. That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia. Browsers with the appropriate proxy can reach these sites, but others can’t. No, darknet carding sites engage in illegal activities related to fraud and identity theft, making them highly illegal.
Can I Report Suspected Darknet Activity?
Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P. Onion links have no regular domain names registered under the domain name registry. Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser.