It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals. By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. While it provides unparalleled privacy, it also harbors potential dangers.

Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. Utilizing The Onion Router (Tor) network, these sites encrypt user data, providing layers of protection much like an onion. Users access these sites via the Tor Browser, which conceals their identity and location. Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds. His articles have appeared in many respected technology publications.
Related Articles From The Business Security Section
Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer.
Secure Registration Process
These currencies enable seamless cross-border transactions without the need for intermediaries, reducing costs and increasing efficiency. Monitoring active marketplaces offers early access to malware kits, credential dumps, and fraud tools. Tracking vendor migration—such as from Archetyp to Exodus—provides insight into tactical shifts. Focusing intelligence collection on specialised marketplaces yields better ROI for threat detection and proactive defence. In 2025, darknet marketplaces primarily accept Monero (XMR) and Bitcoin (BTC).
The Silk Road Marketplace
It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web. If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more.
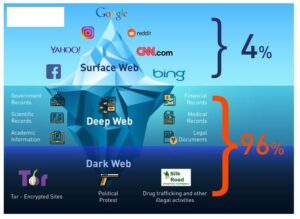
A network browser gives you access to sites with the ‘.onion’ registry operator. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.

Silk Road 20

This handy feature monitors the dark web for signs that your login details or other personal info have been leaked. However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere. For instance, after the closure of Genesis Market, its website came back after a few weeks.
These advancements will further solidify their position as a secure and reliable option for users worldwide. User reviews and vendor ratings play a critical role in maintaining trust within these markets. Platforms like Empire Market 3.0 have implemented advanced feedback systems, allowing users to evaluate vendors based on product quality, delivery speed, and communication. This transparency fosters a reliable trading environment, encouraging repeat transactions and long-term relationships between buyers and sellers. Darknet marketplaces in 2025 illustrate a resilient and evolving underground economy. Major active platforms include Abacus, Russian Market, BriansClub, and Exodus.
But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously. The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures. The release of Freenet in 2000 is considered by many as the start or founding of the dark web. University of Edinburgh student Ian Clarke created Freenet as a thesis project.
- This market is not open to the general public and is subject to a thorough vetting process to ensure its security.
- Since its spark, it’s weathered storms—DDoS barrages, law’s prying eyes, and the darknet’s own treachery—to rise as a shadowed titan.
- Besides, victims of crime may want to hide their identities from their perpetrators.
- Additionally, using antivirus software and strong passwords can further protect you from potential threats.
- It is used by many for buying or selling items that are prohibited on the regular internet, like fake IDs, illegal drugs, and stolen data.
Top Markets
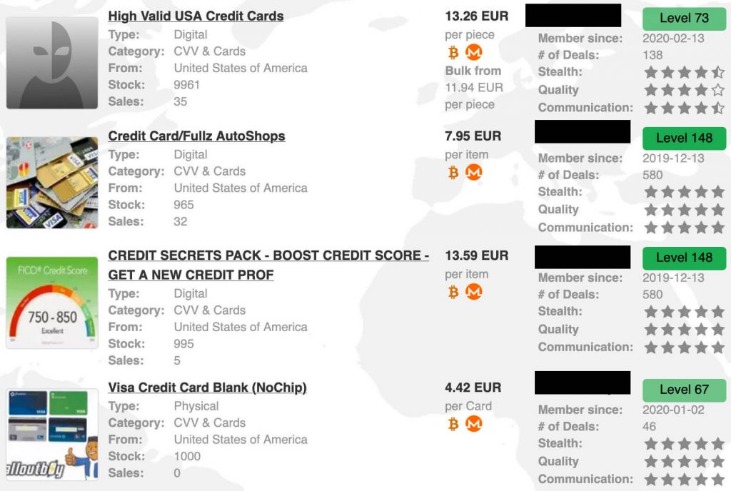
You can find items like digital goods, software, and even collectibles. Some markets have services related to cybersecurity, while others might list more controversial items. The selection depends on the marketplace, and not everything found is legal. Black Ops Market prioritizes user security through comprehensive protection measures that go beyond standard darknet marketplace security protocols. Our multi-layered approach ensures that every aspect of your interaction with our platform remains secure, private, and protected from potential threats.
Navigating Darknet Market Links Safely
This service not only masks your IP address but also encrypts your data, adding an extra layer of security. By using Forest VPN, you ensure that your internet service provider (ISP) and other potential eavesdroppers cannot trace your online activity back to you. Discover how to safely access dark web marketplace links while ensuring your privacy and security online.
However, you can trace its roots to the development of technologies like the Tor network or Freenet. In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing.

Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing. Also a contributor on Tripwire.com, Infosecurity Magazine, Security Boulevard, DevOps.com, and CPO Magazine. Always use a fake name and a temporary email address when you buy something from the dark net shops. You can even use a secure email provider or a burner email address whenever you visit the dark web.
Even browsing these sites can put you at risk of malware infections or attract unwanted attention from law enforcement. BidenCash became known for regularly leaking huge amounts of stolen credit card data and personal information — often for free. This strategy, along with a strict sign-up process, helped it grow fast. The goal is simple — make financial fraud easy and get as much attention as possible. The dark web market changes all the time, but some dark web marketplaces have made a name for themselves as the biggest and busiest spots.

Nevertheless, most people on the internet do not need to communicate or venture into the dark web. The dark web is a hidden section of the internet that you cannot reach with common search engines like Bing or Google. The only way in is through the use of special software that renders all users anonymous and untraceable. Imagine an underground version of your favorite online marketplace, somewhere hidden, exclusive, and often operating outside legal boundaries. It is similar to an online store, except it’s not the type you’ll find with a quick Google search. These marketplaces are full of risks (security, legal, ethical issues – all of them).