Information in the listings was entered into a spreadsheet for data analysis and statistical calculations. With the growing threat from cybercriminals who sell stolen credit card information on the deep web and dark web, businesses need to stay ahead of the game. Over the years several advanced tools have been developed to help track and prevent such fraudulent activities. Stolen credit cards and their details are added and bought on these shops on an hourly basis, and more and more markets launch a matching forum and/or a Telegram channel to keep expanding and supporting criminal online activity. Criminals are abusing mainstream social media applications to advertise stolen data, in this case by brazenly posting full stolen credit card data to the Threads app. Financial institutions can proactively strengthen their defences by integrating intelligence derived from FraudAction.
- Companies such as my #1 pick, Identity Guard, can monitor your Social Security number (SSN) and alert you if it is being sold on the dark web or being used to open an account.
- The best way to protect yourself from credit card theft is to be vigilant about monitoring your credit card statements, using strong passwords, and avoiding public Wi-Fi networks for financial transactions.
- The key is catching this activity before large volumes of card data make it to market.
- Skilled hackers can take the stolen credit card number and replicate it onto a blank card using specialized equipment.
Your Cookie Settings Are Preventing This Third Party Content From Displaying
“The shadow economy that prevailed in Russia in the ’90s-2000s will return.” The freely circulating file contains a mix of “fresh” cards expiring between 2023 and 2026 from around the world, but most entries appear to be from the United States. With contactless payments, thieves can use radio frequency identification (RFID) technology to skim your card’s information if they’re close enough to the card reader.
- The hackers’ group advertised a massive collection of payment card details for sale, dubbed “BLAZINGSUN,” at $17 per card.
- And all payments stakeholders can visit Visa’s website to see public reports and press releases regarding malware, indicators of compromise, mitigation, and protection.
- The attackers obtained approximately 2.55 million records containing basic business contact information such as company names, phone numbers, and related notes.
- This initiative has distributed over $4 million to participants who helped trace $40 million in stolen crypto and prevent further laundering.
NSW Department Of Communities And Justice Data Breach
However, it’s important to note that accessing the dark web can be dangerous and is not recommended unless you have a specific reason to do so. Her key role is to connect with members in the community about Ideal CU through different platforms. Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends. First, a compromised private key let them create 200 million tokens; despite PlayDapp’s quick response, the attackers returned to mint another 1.59 billion tokens, vastly amplifying the losses.

Microsoft Teams Vulnerability Could Let Attackers Access And Alter Messages

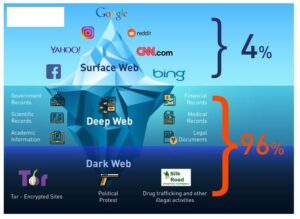
Dark web credit cards are often sold on online marketplaces, which can be accessed through specialized browsers like Tor. Tracker apps offer a powerful way to keep tabs on credit card activity. These tools scan transactions in real-time, flagging any suspicious charges instantly. 1 This quick notice helps spot fraud fast, before major damage occurs.
Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords. Credit card details can be sold as digital items on the dark web, with the basics costing around $17.36. Physical cards, on the other hand, are cloned from stolen online details and can be used to withdraw cash from ATMs.
The Easy Way In/Out: Securing The Artificial Future, Trend Micro Security Predictions For 2025
The breach potentially exposed customer data inadvertently copied to the repositories for debugging purposes. In March 2025, the New South Wales Department of Communities and Justice (DCJ) experienced a significant data breach involving unauthorized access to the state’s secure online court registry system. An unknown hacker accessed at least 9,000 sensitive court documents, including apprehended violence orders (AVOs). The breach primarily involved “credential stuffing,” where hackers used previously stolen passwords to log into accounts. On March 21, 2025, a threat actor known as “rose87168” was discovered selling 6 million records exfiltrated from Oracle Cloud’s Single Sign-On (SSO) and LDAP systems. The compromised data included Java KeyStore (JKS) files, encrypted SSO passwords, key files, and enterprise manager JPS keys.
Ready To Explore Web Data At Scale?
In a similar study earlier this year, we noted an average price of 3.13 cents per dollar in the account. So unlike credit cards, prices for PayPal accounts and transfers have gone up during the pandemic by 293 percent. “I’ve been able to get all-inclusive trips and holidays, and my Netflix accounts and Spotify,” D2 said.

Regularly Monitor Your Financial Statements
Plus, scammers do get caught—often ending up with a lengthy prison sentence or hefty fine. Most banks and credit card vendors offer you the option to receive fraud alert notifications—email or text alerts—warning you of potential card theft. Scammers start by prompting users to download malware, which is often disguised as a harmless email attachment. Once it starts running on your machine, the malware collects data such as used keystrokes, browser history, and shopping habits.

In July 2025 Allianz Life disclosed a breach affecting 1.4 million United States customers through a third party CRM platform. Around the same time Qantas revealed a contact center breach impacting up to six million customers, caused by social engineering on external IT systems. Using a list of 500 million email addresses, they identified over 15 million users and compiled data including email addresses, names, usernames, and activity logs.
Dark Web Monitoring Tools
In early August 2021, a threat actor known as AW_cards published a data leak containing details of approximately one million stolen credit cards on several Dark Web hacking forums. The leak was shared free of charge as a promotion to the threat actor’s new carding marketplace, named AllWorld Cards. In recent years, I’ve observed some shifts in how carding is carried out—changes that mirror broader developments in both technology and threat intelligence research. Notably, cryptocurrency has become a valid option for carding operations, whether through exploiting stolen crypto wallets and accounts or using stolen credit card details to purchase cryptocurrency. These details often land there after data breaches, phishing attacks, or malware infections that steal information from unsuspecting users.
Detecting Credit Card Fraud: What To Look For
This opens the door to applying for loans, creating fake IDs, or taking out credit cards in your name. It can take months—or even years—to recover from this kind of identity fraud. Recent studies reveal that 63% of U.S. credit card holders have been victims of fraud, and over 50% experienced it more than once. With data breaches happening more frequently, your credit card details could already be circulating on the dark web—without your knowledge. In August 2024, the U.S. healthcare sector reported 92 new data breaches, affecting approximately 5.98 million individuals.
Nearly One-third Of Irish Firms Paid A Cyber Ransom In Last Year
A covert communication app used by US government officials to archive encrypted messages has been compromised. The app, a customized version of Signal created by Israeli company TeleMessage, was intended to meet federal archiving requirements. However, a hacker gained access to an AWS-hosted server within 20 minutes and exposed unencrypted data intended for archiving. After Fowler reported the issue, the hosting provider took the database offline. No one knows who owned it or whether it was leaked by mistake or dumped intentionally. Sepah Bank, one of Iran’s major state-owned financial institutions, suffered a cyberattack in June 2025 amid active military and cyber clashes between Iran and Israel following recent strikes and retaliations on both sides.