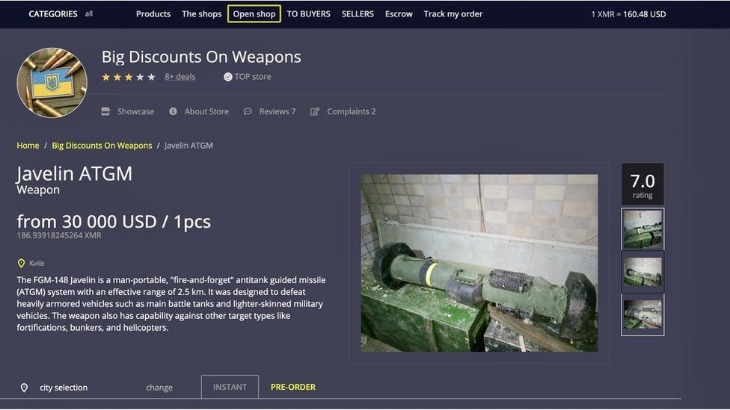
It is one of the most active and up to date markets and always provides new and updated malware and data. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet. Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents. Onion sites can be safe in terms of privacy protection due to strong encryption, but they also host a significant amount of illegal content and scams.
Since the beginning of DWMs’ activity, there has been a shift in the law enforcement approach from focusing on market admins towards sellers and buyers9,13. For instance, a recent London Metropolitan Police (MET) investigation examined the transactions of a seller profile on a DWM10. The investigation uncovered a local criminal organization linked to a large international drug supply operation. Therefore, key actors in the ecosystem of DWMs may play important roles in broader criminal networks. In general, by understanding the operation of key players within the DWM ecosystem, our work highlights how appropriate strategies can be designed to counteract the online trade of illicit goods more effectively.
What Is A Dark Web Alert? A Guide For Businesses
You can even use a secure email provider or a burner email address whenever you visit the dark web. The website looks organized and has a clean, sleek, easy-to-use UI. You can find featured listings on the homepage and browse the products of your choice. There’s also a search bar that you can use to search for any particular product or vendor. It doesn’t use JavaScript, meaning the website won’t track your activities or exploit vulnerabilities.
CNBC Newsletters
With the increased reliance on computers and the Internet, the market to exploit it grew as well. With the growth of websites built by Internet startups and enthusiasts, closed-source tools were developed and sold to allow script kiddies and beyond to scan, analyze, and attack those websites. Some even granted some time-shared access to botnets like ZeuS to bludgeon websites with unrelenting DDoS or focused Layer-7 attacks, like authentication brute forcing or comment spam. Of course, these tools eventually found themselves on free file sharing platforms like KaZaA and LimeWire, but not before they found plenty of sales on online black markets first.
Why Are All The Darknet Markets Down
These platforms sell everything from drugs and fake IDs to weapons and hacking tools, resembling a digital black-market bazaar. Before we delve into the mechanics of staying safe, it’s crucial to understand what the black market really is. Often viewed as a shadowy underbelly of the internet, it offers goods and services that are not available through traditional channels.
Use Active Monitoring Of Financial And Identity Theft

The classification is performed in five steps (see Fig. 1), as detailed next. In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks. Protecting against this is as complex as asking, “How do we end poverty?” For an end-user, good security practices are a major first step.
Dark Web Phishing Kits: How Hackers Sell Ready-Made Scams
The website allows a personalized searching experience, where you can search according to your geographical location, country-specific, and keyword or price-specific search results. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests. However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere. For instance, after the closure of Genesis Market, its website came back after a few weeks.
- Then, we reveal a concentration of activity around an elite group of participants, where a large fraction of the trading volume is driven by a small number of players.
- The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it.
- Also, use an effective antivirus program to check threats if you decide to download files.
- If you purchase something from such shops and make payment through conventional payment methods like your bank transfer, credit/debit card, or PayPal, you can be caught easily and face legal consequences.
- The deep web, invisible web, or hidden web sounds like a mysterious depth of the world – but the concept is quite simple.
I2P can only be used to access hidden sites that are only available on the I2P network. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. Hacker services against banks and other financial institutions are offered there. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better.

How To Avoid Phishing Scams And Malware Threats
The marketplace extensively vets vendors listed within its deep web environment that offer a wide range of product portfolios, including security solutions, digital services, and specialized equipment. It stands as a reliable alternative to the defunct Alphabay Market as it continues to position itself as the premier source for advanced privacy-focused digital commerce. Awazon Market is a top-tier dark web marketplace with claims to revolutionize secure anonymous commerce. It offers a wide range of goods and services with robust anti-DDoS protection (with military-grade security protocols) and no JavaScript, ensuring privacy and uptime.
- Besides this, it supports wallet-less transactions and accepts payments through Bitcoins, Litecoin, Monero, and Zcash.
- Users and cybersecurity professionals alike must stay informed and prepared to navigate this rapidly changing digital frontier.
- As law enforcement agencies’ tactics improve, some markets respond by introducing more security features, like mandatory encryption or invite-only access.
- Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together.
Then, after operation Bayonet, the number of sellers in all categories and multisellers significantly drops, as shown in Fig. Notably, the number of multisellers suffers the largest drop of \(-99\%\) by the end of the first quarter of 2018. Interestingly, while the other categories of sellers show signs of recovery relative to their previous levels, the number of multisellers remains low after that shock (see Supplementary Information Section S4). By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked data is exploited.
This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. Unfortunately, it requires you to have an invitation code to create an account. This means you have to know someone who is already using the platform.
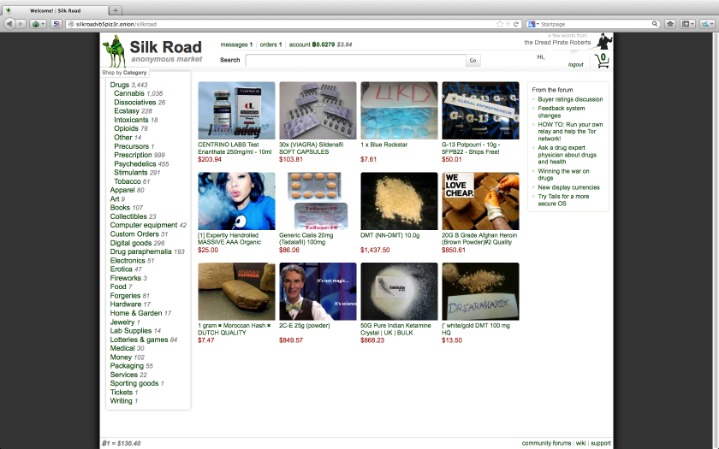
And (c) is the dark web, which is the part of the deep web that isn’t indexed by search engines and requires special tools like Tor Browser to access. Blockchain even has an HTTPS security certificate for even better protection. Law enforcement agencies and international coalitions play a critical role in countering dark web activities. Operations such as the takedown of the Silk Road and AlphaBay marketplaces demonstrate the global effort required to dismantle these illicit networks.
Therefore, we analyse the temporal network where nodes are the active markets and an edge between the nodes represents the number of multibuyers between them, what we henceforth call the multibuyer network. The structural change seen in the multiseller network is not observed in the multibuyer network, as show in Fig. The evolution of the multibuyer network follows a similar pattern to the multiseller network until 2015, despite a stronger polarization around Hydra instead of AlphaBay during 2017. However, after the operation Bayonet, although the network shows a decrease in connectivity, it still remains highly connected and with a large number of active multibuyers. Moreover, the network had already fully recovered by 2019 showing a strong resilience against external shocks.



