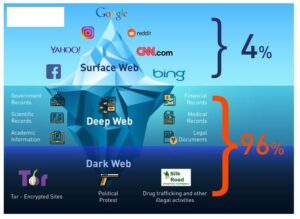
The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search. Typically, any reference to the visible web will be to common websites with a familiar internet domain extension. Google considers the majority of the content on the entire web highly irrelevant and useless to its users.

All you’ll need is an 8GB thumb drive, an installation package, and a couple of minutes to get things up and running. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web. Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination.
Vorm Web Search Engine
For instance, a factory employee can secretly slip away with one and sell it on the darknet markets. In this darkest corner of the internet, that gun becomes an illegal weapon. That’s exactly what happens when it comes to the dark web marketplaces. We understand the curiosity to venture into the dark web, but you also need to understand that it’s never safe to venture into this portion of the internet without fully understanding what it entails. Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform.

Established in 2020, Awazon Market has quickly become one of the most famous darknet marketplaces. The market claims to provide secure and anonymous commerce services. You can find a lot of goods and services packed with stealth high-level encryption, no JavaScript, and anti-DDoS protection. To find .onion links for dark web sites, you’ll need to use a dark web search engine.

Real-World Examples: Data Breaches Feeding Dark Web Black Markets
For instance, cybercriminals can buy credit card details with a $5,000 balance for just $110. Saheed Aremu passionately advocates for digital privacy and cybersecurity in the modern digital age. As one of PrivacySavvy’s resident VPN experts, he guides readers on protecting their online information and anonymity. Saheed earned his degree in Technology and Ethics from the University of Lagos in Nigeria.
Dark Web Monitoring And Identity Theft Protection At Your Fingertips
The Tor browser allows you to browse the internet anonymously and visit inaccessible sites. Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there. As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across. Immediately close your entire Tor Browser window (not just that active tab).
Secure Your Connection

Accidental leaks at the Tor entry nodes can potentially expose your IP address. A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. If you are in a position to report the incident safely, you should report it to the authorities immediately. It’s recommended not to be too vigilant here and leave the investigation to the professionals.
We The North Market (Best For Secure Transactions & Low Fees)
Onion sites may offer secure access to cryptocurrency wallets or anonymous email clients. It’s a bit of a contradiction to talk about search engines for dark web sites because, by definition, these are not sites that get indexed by traditional search engines. Many dark web search engines on the darknet suffer from spam, because these spammy sites want to be indexed and found by the search engines as opposed to genuine onion sites. Vorm Web focuses on quality over quantity and splits findable results into three security categories, from secure to risky. This trove of stolen data included names, addresses, Social Security numbers, and phone numbers, leaving millions of individuals vulnerable to identity theft.
- Cybersecurity has to also cover everything physically on your computer too—which law enforcement or government authorities might have the right to seize if they come calling.
- The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers.
- There are several whistleblower sites, including a dark web version of Wikileaks.
- Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny.
ChromeAlone – Chromium Browser C2 Implant For Red Team Operations
When both buyers and sellers are anonymous, the credibility of any ratings system is dubious. Ratings are easily manipulated, and even sellers with long track records have been known to suddenly disappear with their customers’ crypto-coins, only to set up shop later under a different alias. Silk Road was once the most well-known dark web marketplace, but after its shutdown, many new markets took its place. Today, buyers and vendors look for reliable alternatives that offer security, escrow protection, and a strong vendor community. It’s a place where you’ll find data leaks and illegal trades, but also legitimate, legal online activities users want to carry out without attracting the attention of law enforcement agencies or governments. It’s a part of the internet that’s less regulated and more shadowy, for better and for worse.
Bohemia is a modern dark web marketplace with a great user interface that is easy to use and navigate. It asks you to pay the merchant fee if you want to sell something, preventing the buyers from getting scammed. However, in April 2022, this site went offline after American and German federal government law enforcement agencies seized the website servers. Some alternative links are available, providing access to the marketplace. It’s recommended not to use new alternative links as they could just be planned exit scams.
While there are legitimate products and services in the darknet markets, often, these markets deal with illicit goods and services like drugs, fake documents, and hacking services. Their presence can make you wonder why darknet markets and not just the regular online stores. Therefore, you must know how to access dark web marketplaces safely (covered later in this article). ASAP is a tech nerd’s playground—accepting BTC, LTC, ZCash, and Monero, it’s got options for days.
- In addition, Darknetlive has a list of dark web vendors, which is very convenient — it offers detailed information about each vendor, including .onion addresses (in alphabetical order) and FAQs.
- Then, simply click the operating system that you are using and download the file.
- Although ProtonMail also exists on the clear web, accessing it via Tor provides an extra layer of privacy if you don’t want to leave a trace of you even using ProtonMail.
- On one hand, it offers privacy for whistleblowers, journalists, and citizens in oppressive countries.
- The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption.
They provide criminals with access to everything they need, from launching attacks to stealing data, etc. The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities. Of course, the promise of secrecy and unfiltered access might lure you in, but those same features are what make the environment so risky.