Many countries in the world have suffered from different forms of terrorist attacks in the last few decades. Terrorism is a big problem that needs to be addressed otherwise the country’s security and financial situation will get worse. They also want to avoid regulations that could harm their business models. When the regulatory authorities and governments start talking about this seriously.
Dark Web Sites Offering Financial Services
Your search activity isn’t stored, and you get decent answers for most queries without all the tracking. The search engine is also available on the dark web and offers an additional layer of anonymity and privacy with fast search results. Dark web links are unique .onion URLs that grant access to hidden websites on the dark web, which can only be reached using the Tor browser for privacy and anonymity. This can include gathering information from various sources, including dark web forums, and analyzing trends related to cybercrime.

Average Number Of Tor Users Per Day By Country
By familiarizing yourself with these networks and protocols, you gain a clearer understanding of the diverse strategies people use to stay hidden online. But despite its many benefits, it’s sadly just a matter of fact that the dark web can be a dangerous place. Near total anonymity and a complete lack of regulation can easily attract criminality, and onion sites can harbor malware such as ransomware or spyware. SecureDrop uses Tor to provide a safe way for whistleblowers to contact various news outlets. Prominent organizations like The Guardian, The New York Times, and ProPublica have implemented it. The software requires two-factor authentication to receive what’s been uploaded by the whistleblower and allows two-way communication between the anonymous contact and the media outlet.
Dark Web Sites Providing Software And Tools
This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacyRadar.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. In addition, it has an automatic kill switch (Network Lock) that stops traffic if the VPN connection fails. Accidental leaks at the Tor entry nodes can potentially expose your IP address. Also, use an effective antivirus program to check threats if you decide to download files. You can check out this guide on the best antivirus software applications today.
Encrypted Messaging Apps And Private Communities
While the Tor Browser provides strong anonymity, using a VPN (Virtual Private Network) alongside it adds an extra layer of security and privacy. A VPN encrypts your internet traffic before it enters the Tor network, hiding your Tor usage from your internet service provider and shielding your IP address from the first Tor relay. This setup can help prevent network-level surveillance and reduce risks in environments where Tor use might be flagged or restricted.

The Best Tor And Onion Links

Keybase is an encrypted communication platform that enables secure file-sharing and messaging using public key cryptography. Though not specifically a .onion service, Keybase integrates well with privacy-focused ecosystems like Tor. It offers features like encrypted communication for chats and file sharing, making it popular with privacy-conscious individuals. Sci-Hub provides free access to scientific papers, with millions of documents.
The Best Dark Web Links — Safe & Verified Sites In 2025
It’s maintained by an independent organization committed to digital privacy and security. It runs an onion site to help like-minded people mobilize more securely and anonymously. To access them, copy and paste the hyperlinks provided into the Tor browser. In exploring the top 10 dark-web marketplaces in 2025, we’ve examined their core operations, diverse use-cases, inherent risks, and evolving trends.
- The complexity and randomness of onion addresses make it easy for scammers and malicious actors to create spoofed versions of popular sites.
- Still, the Tor dark web browser also remains a vital tool for privacy-conscious users.
- Safe browsing on the Hidden Wiki requires a combination of technical precautions and behavioral discipline.
- It wouldn’t just impact the dark web links, but its powerful impact will also spread to the physical world.
- The Bitcoin core website posts the latest updates to the open-source Bitcoin software, which is programmed to decide which blockchains contain valid transactions.
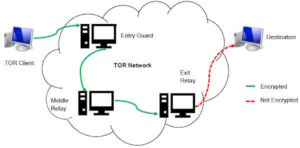
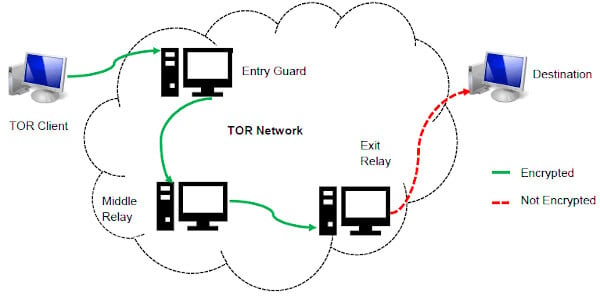
The Tor version works exactly the same but keeps your identity even more protected. Onion sites are slower than regular websites due to Tor’s privacy-focused design. Tor uses multi-layered encryption and routes data through multiple relays (entry, middle, and exit nodes), which increases latency to enhance anonymity.
What Is The Deepest Search Engine?
Just as you explore hidden corners of the internet, you need to secure your data on the go. Easily initiate data encryption on your external drives and disks, ensuring compliance with your specific company policies. Encryption-2-Go offers controlled encryption, container-based or directory encryption, and even detects existing BitLocker To Go encrypted drives. With configurable user selection dialogs, it provides a user-friendly experience while maintaining strict security.

The protection will apply to all your devices so you can browse and send communications without fear of your data being compromised. Take advantage of Prey’s no-risk, 14-day trial and give you and your business the protection it deserves. Credential-based attacks are a form of cyber threat where attackers use stolen or forged credentials to gain unauthorized access to systems and data.
Infostealers and drainers will likely be increasingly promoted as subscription-based services, with traffers aiding in their distribution via scam pages and phishing schemes. Following stricter bans on Telegram channels hosting cybercriminals, experts predict a resurgence of activity on dark web forums. Threat actors may also manipulate old or publicly available data to generate hype and damage reputations.
Initiatives include enhanced monitoring of cryptocurrency transactions and international collaborations to dismantle illicit online marketplaces. While these measures have led to the shutdown of several high-profile platforms, the decentralized nature of the dark web poses ongoing challenges to regulatory enforcement. For instance, dark web websites could be infected with malware, or designed as scams to gather stolen data. Tools such as VPNs can make it somewhat safer to browse, but people should still exercise extreme caution whenever visiting web pages on the darknet.
Proliferation Of AV Evasion Tools (Cryptors)
SecureDrop is an anonymous file-sharing platform designed for secure communication between whistleblowers and journalists. While anyone can use it, it’s built for high-stakes exchanges, making it overkill for routine file sharing or data backups. Major news outlets like The New York Times, The Economist, and The Guardian host SecureDrop instances on the dark web to give sources a safe, anonymous way to share sensitive information. But while anonymous email services can help protect your identity, they don’t make you immune to threats like email spoofing or social engineering.
Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators. Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.