
It has gained a reputation for being a reliable source of high-quality data for cybercriminals. Due to its extensive inventory and reputation for reliability, Brian’s Club has maintained a significant presence on the dark web. Quality and validity of the data it provides justify its higher cost over other marketplaces.
What Are EWallets And How Safe Are They?
- Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine.
- To access the dark web safely, it’s necessary to use a dark web browser like Tor in combination with trusted dark web directories and search engines to help you find reliable sites.
- The Hidden Wiki is a directory hosted on the clear net (also called the “surface web”) that contains a list of .onion links for many of the best dark web websites.
- Though a large volume of traffic visits on the open web every day, it only represents 4% of the content on the internet.
The deep web refers to the parts of the internet that you can’t reach through search engines like Google Search. While this includes the dark web, the deep web also includes pages that you can only find if you register or sign in, like most content provided by Gmail and Facebook. The dark web is a part of the internet that lets people hide their identity and location from other people and from law enforcement. As a result, the dark web can be used to sell stolen personal info. The dark web is a complex part of the internet, and specialized search engines are essential for safely experiencing it.
What Is The Surface Web?
In this volatile ecosystem, recognizing the dynamic nature of the dark web is half the battle. By acknowledging that services, communities, and security measures are in constant flux, you can better position yourself to respond effectively. One of the most insidious dangers on the dark web is not just technical malware or hidden exploits, but the human element—scammers and con artists who rely on psychological manipulation. Social engineering attacks leverage trust, fear, curiosity, or urgency to trick users into revealing sensitive information, transferring funds, or compromising their anonymity. By learning to recognize these ploys and adopting defensive habits, you can significantly reduce the risk of becoming a victim. While no approach guarantees complete safety, a careful and skeptical mindset serves as one of your most valuable tools on the hidden internet.
Torch Search Engine
However, it also lingers all across the dark web to infect unsuspecting users just like it does on the rest of the web. The dark web was once the province of hackers, law enforcement officers, and cybercriminals. However, new technology like encryption and the anonymization browser software, Tor, now makes it possible for anyone to dive dark if they’re interested. While no single tactic is foolproof, a layered approach—combining technical, operational, and psychological defenses—greatly improves your safety and confidence when navigating the dark web. The Excavator search engine digs through the depths of the dark web, offering an expansive view of indexed content.
Top VPN Deals
Even data which is not used for ads, such as Gmail data, is still collected and could therefore be leaked in a breach or government data request. We founded Proton in Switzerland in 2014 specifically to resist mass surveillance and abuse of personal data by US tech companies. If you want to use the internet without giving up your most sensitive, valuable data, many European services offer a privacy-forward alternative. However, there are plenty of legitimate reasons to use the dark web. You can read ProPublica(new window) or The New York Times(new window), check your email in Proton Mail, or browse your Facebook wall(new window).
Connect With Us
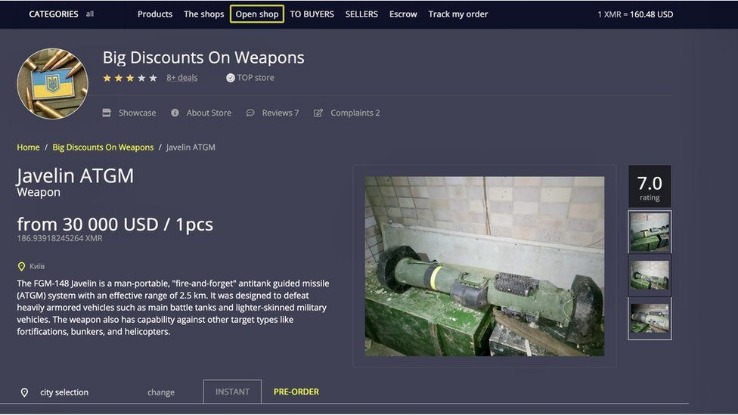
As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web. A lot of transactions are handled via cryptocurrencies such as Bitcoin, which is relatively (but not completely) private and anonymous. Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now).

All our revenue comes from Proton customers who upgrade for more storage and premium features. But there are simple ways to create an email address privately that are just as secure, if not moreso. Reclaiming your privacy doesn’t mean disconnecting or going into hiding. And it starts with stepping outside the system that profits from watching you and into one that’s built with you as the top priority.
Reuters, Fox, NBC, CNN – all of them keep open dark web channels to receive anonymous tips from whistleblowers. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. Hidden Facebook is hardly the only social media client on the dark web. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game.
What Is The Dark Web? The Good And Bad Of The Internet’s Most Private Corner
Organizations constantly face the risk of data breaches, but the existence of the dark web amplifies this risk. For instance, if a company suffers a quiet data breach, its users’ personal information will likely end up for sale on a dark web marketplace. Carrying on with the analogy, big search engines could be considered like fishing boats that can only “catch” websites close to the surface. Everything else, from academic journals to private databases and more illicit content, is out of reach. This deep web also includes the portion that we know as the dark web.

This is accompanied by the Network Lock kill switch that also prevents IP leaks. We love it because of its simplicity, which, as you saw, lets you visit the dark web in seconds. NordVPN’s NordLynx protocol is more than secure, with a certified no-logging policy that guarantees no logging and storing of your sensitive data. It encrypts your traffic right away, which is beneficial if you don’t want your ISP to see you’re using Tor. Some countries frown upon dark web usage, so it’s good to have your back covered by a reputable VPN service. Your ISP can see that you’re connected to Tor, as the encryption takes place AFTER you connect to the browser.
The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world. It will offer you an additional layer of encryption to access the deep parts of the internet. If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more. The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article). Though people usually think of dark websites as the wrong online place, that’s not the complete truth.
Use A Trusted VPN
In the dark web, you can come across forums, markets, and hidden communities. These areas usually need specific darknet browsers such as Tor, which bounces the traffic through several layers or nodes to avoid the identification of IP addresses. ’ it is crucial to identify it as a two-sided phenomenon–a safe haven for legal proponents of privacy and a home for cybercriminals. The privacy offered by the Tor browser is important in the current digital age. Corporations and governing bodies alike currently participate in unauthorized surveillance of online activity.



