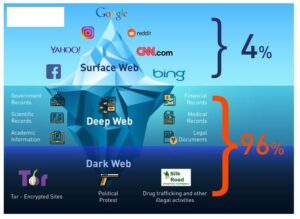
It’s a place where you’ll find data leaks and illegal trades, but also legitimate, legal online activities users want to carry out without attracting the attention of law enforcement agencies or governments. It’s a part of the internet that’s less regulated and more shadowy, for better and for worse. Immediately change your passwords, enable two-factor authentication, and notify your bank or credit card provider if the leaked information includes your financial data. You should also consider freezing your credit to prevent identity theft. If you’re using a browser like Tor and visiting .onion websites that aren’t accessible through regular search engines or browsers, you’re likely on the dark web. These sites often look basic or outdated, and their URLs are lengthy strings of random letters and numbers.
Final Thoughts: Is The Darknet Dangerous?

Despite its name, the marketplace operates primarily in English and serves a global audience. It has gained a reputation for being a reliable source of high-quality data for cybercriminals. The dark web is only accessible through specific software like Tor (The Onion Router).
Did The Silk Road Marketplace Go Under?
You can even find things such as BIN checkers and PayPal cookie converters. Another reason the Russian Market is so popular is that it’s pretty inexpensive compared to other dark web marketplaces. Of course, not all the popular and widely-used dark web sites and things like marketplaces on the dark net are illegal. Some use them due to privacy concerns, such as journalists talking to informants or whistleblowers, while others may simply want to protect their confidential information from observation or tracking.
Tor Browser, built on Firefox, encrypts your traffic across 3+ relay nodes, enabling access to .onion sites. In 2025, it powers 2.5M+ daily users, with Germany leading in usage (followed by the U.S.). Today’s markets reflect a decade of evolution, balancing user demand with operational security against an ever-present cat-and-mouse game with authorities.

In the first arc of the anime series Lupin the 3rd Part V, Lupin III steals digital currency from the “Marco Polo” darknet market. For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy. For operations security he suggests avoiding storing conversation logs, varying writing styles, avoiding mobile phone-based tracking and leaking false personal details to further obfuscate one’s identity.
Unfortunately, that as well didn’t stop other darknet markets from rising. The sad reality is the fact that law enforcement agencies can’t track and prosecute perpetrators or even take down such content given the anonymous nature of the dark web. As much as authorities work hard to shut down various sites, it shows what the dark web is capable of doing if left unchecked.
- On average, the marketplace consists of more than 11,000 items and 1000 vendors.
- Another reason the Russian Market is so popular is that it’s pretty inexpensive compared to other dark web marketplaces.
- Check around with other users and ask if they know anything about the new marketplace.
- Notably, Abacus explicitly forbids highly dangerous goods, including weapons, explosives, and exploitative material, which has helped maintain a relatively favorable reputation among its user base.
Stolen Data And Identity Theft
Dark markets, as well as various other services within darknets, are hosted as ‘hidden services’. This means that the servers providing these services are only accessible via Tor and do not have a public IP address or domain name. Hidden services can operate while keeping the physical location of the server hidden, which makes tracking and shutting them down considerably more challenging.
Additionally, Joules’ commitment to sustainability and ethical practices resonates with environmentally conscious consumers, fostering trust and brand loyalty. In some cases, established sellers on closed-down markets are welcomed onto new markets as digital “refugees” and have joining fees waived. Compared to its predecessors, Archetyp enforced enhanced security expectations from its users. These included an advanced encryption program known as “Pretty Good Privacy” and a cryptocurrency called Monero. Unlike Bitcoin, which records every payment on a public ledger, Monero conceals all transaction details by default, which makes them nearly impossible to trace. The durability of these markets tells us that if policing responses keep following the same playbook, they will keep getting the same results.
- Even if you’re using a private, anonymized crypto wallet, there are other ways your identity can be revealed—even if it’s something as simple as letting a personal detail slip in an instant message.
- The Torrez market is one of the biggest dark net marketplaces, also called a community-driven marketplace.
- In 2021, German and Finnish law enforcement seized the computer server hosting Monopoly and took it offline.
- Search engines do not index these sites and use domains like .onion (for Tor) or .i2p (for I2P).
Alternative Anonymous Networks

Its 13,000+ users and 1,100+ vendors rely on a secure, fast-paced trading network. Alphabay reigns supreme with 60,000+ listings and $20M monthly trades, dominating 20% of darknet commerce via BTC and XMR. Its 25,000+ users and 3,000+ vendors trust its unmatched escrow and scale.
Keep Your Identity Hidden
As terrible as its reputation may be, some vendors sell legitimate goods or services. Some customers even use the dark web to make anonymous purchases, especially in areas where privacy is a huge concern. So, not everyone who shops there is looking for something illegal.
Transactions within dark markets predominantly involve cryptocurrencies like Bitcoin, Monero, or Ethereum. These digital currencies provide a degree of anonymity, as transactions are recorded on a public ledger but do not directly link users to their real-world identities. To purchase illicit goods or services, users deposit cryptocurrency into an escrow system or directly to the seller, and the cryptocurrency is held until the buyer confirms the satisfaction of the transaction.
Top VPN Deals

Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net. Despite using a VPN, there’s always a risk of the VPN leaking your IP address through DNS or WebRTC leaks or misconfigurations when on a dark web forum or marketplace. Therefore, you must run an IP leak test to ensure that the VPN is working completely fine and is not risking your digital security.
Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet. However, it’s much harder to get at the people who are doing the uploading and downloading. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for.
The Escrow Process
They operate similarly to regular e-commerce sites but use cryptocurrencies for transactions. Most dark markets have user review systems and vendor ratings to establish trust. Law enforcement regularly shuts down these markets, but new ones continuously emerge.
How To Gain Safe Access To The Dark Web Marketplaces
The Monopoly Market takedown was one of the largest law enforcement actions taken against a darknet marketplace. The resulting arrests overshadowed the 150 arrests made following the takedown of DarkMarket in 2021, and 179 following the takedown of Wall Street Market in 2019. It scans darknet marketplaces and hacker forums to alert you instantly if anything shows up. This way, you can catch any leaks and stop them before they cause bigger problems. The buyers, or “consumers,” are cybercriminals who use these tools to launch illegal activities.