Enable two-factor authentication to avoid malicious actors accessing your accounts even if they get the correct username and password. Ensure your Tor browser is always up-to-date– automatic updates are enabled by default, but if turned off, you should manually update it regularly. As mentioned earlier, many websites consider Tor suspicious and block users entirely. Sometimes, you can access a website but won’t be able to login on your Tor browser.

How To Access The Dark Web Using Tor
With its nifty “conjoin” feature, users can combine different coins in one transaction, covering the user’s tracks and maintaining their anonymity. The wallet is user-friendly and provides robust security, making it one of the best crypto wallets on the dark web. Finally, Wasabi Wallet is non-custodial, meaning you alone can access the encryption keys.
This provides convenience, as it allows you to access onion websites using your regular browser. However, you should use Tor Browser if anonymity is a high priority. While it can’t know your real IP address, it can see your unencrypted data, which may reveal your true identity (although HTTPS(new window) still protects you). Now equipped with an overview of these essential dark web search engines, you’re ready to conduct your own searches confidently and securely. Unlike DNS, which relies on IP addresses to know where to send your traffic, Tor has its own way of allowing you to access a website without ever knowing its IP address.
Platforms
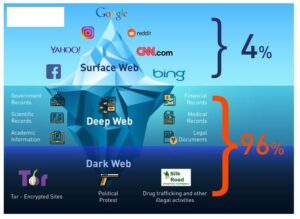
DuckDuckGo is a search engine located in Valley Forge, Pennsylvania, United States. This engine uses information from publicly sourced sites (such as Wikipedia) with the aim of increasing traditional results and improving relevance. Its philosophy emphasizes privacy and not registering user information. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access.
(The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. Make sure that when you download the Tor file, it’s from their official website. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes.
Step 3: Install And Launch Tor
This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers. Crimes range from data theft and selling illegal goods for cryptocurrencies to human trafficking and more severe offenses. Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network. However, its network is still small, and there aren’t many hidden services available yet.
With a variety of server locations around the world to choose from, you’ll be able to navigate the web more privately and access the content you want. Riseup is an invite-only email and communications service that doesn’t hold onto any of the data you generate when you use it. It describes itself as a tool for social change and “a project to create democratic alternatives.” Riseup requires you to have the onion link as well as an invitation. Because dark web sites can only be reached with a dark web browser like Tor browser, the best dark web sites, best onion sites, and best Tor websites are all one and the same. And because they aren’t searchable via Google or Bing, onion site lists are important roadmaps to help users find what they’re looking for on the dark web.
Safely Browse And Verify Onion Sites
- If you’re lucky enough, you can find it on clearnet privacy forums.
- But once the encrypted message goes into the Tor network, your ISP won’t be able to know what you’re trying to access with Tor, or the data that you’re sending.
- The New York Times can also be anonymously accessed via the dark web.
- Clicking on random onion links is quite risky and isn’t recommended.
- That’s where dark web search engines come in — they help you discover hidden websites and make navigating this part of the internet easier.
- Another website is Dread, which is often called the “Reddit of the Dark Web.” It’s a community platform where users can discuss new markets, share onion links, add reviews, and much more.
Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there. Unlike other dark web search engines, DuckDuckGo doesn’t index illegal content, focusing instead on providing safe, unbiased results. This means you can go on the darknet privately while downloading torrents on the side.
How Did We Select These Best onion Sites?
The dark web offers anonymity and privacy, but it also presents significant challenges. While some use it for legitimate reasons like bypassing censorship, others exploit it for illegal activities. Striking a balance between anonymity and accountability is an ongoing debate. By using Tor and a reputable VPN, along with being careful and having the right tools, you can browse the dark web legally and safely. Responsible use protects your privacy while staying within the law, so it’s a safe place to browse for real privacy reasons.

How To Construct Effective Search Queries And Safely Navigate The Dark Web
To access them, copy and paste the hyperlinks provided into the Tor browser. Instead, download Tor, the most secure and user-friendly option for accessing .onion sites. Despite some skepticism about its origins and privacy due to its military development, Tor remains the preferred choice for safe dark web navigation.
It might sound weird that Google doesn’t index these pages, but it does carry some logical sense. Google’s purpose is to show the most relevant information to all of its users quickly and easily. That means that Google wants to minimize the amount of time users spend searching for certain queries.

For those who may be a little faint of heart – we have listed 50 Legit Dark Web sites you can visit. By staying alert, verifying sources carefully, and consistently practicing good security habits, you significantly reduce the risk of encountering threats or compromising your security. While exploring the dark web can offer valuable privacy benefits, it’s crucial to understand common risks and how to manage them effectively. The myth of it being a tool only for nefarious, abject activity counteracts its potential for being known as a tool for access, democracy, and justice. One way to help counteract this myth is to learn more and engage with Tor yourself.
The Tor browser option for streaming comes with eleven channels with varying genres. But, honestly, if you are going on the dark just to enjoy free music, we recommend that you go for free torrent platforms on the surface web instead. The wallet is free, and since it’s open-source, anyone can inspect, verify, and contribute to the code. Keybase is a dark web messaging application that functions much like Signal and WhatsApp, except it is secure and private. You should go to Tor Metrics for real-time information on the ever-growing Tor project — it is literally in the name.
With each random server, your traffic bounces off, and a layer of encryption gets added. These layers upon layers give this network its iconic “onion” name—as the onion itself has layers upon layers. The Tor browser is the most preferred browser for surfing the dark web because it creates encrypted pathways for user traffic, ensuring all the activities are anonymous. However, please note this article is for research and educational purposes only. The dark net is full of notorious hackers, scammers, malware, and other viruses.
It is imperative to stay alert and trust your gut when on the web. Many services that are allegedly offered on the dark web are scams. Some services are genuine; you can get what you want at an agreed fee. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals.