By following these guidelines, you can minimize the potential risks and protect your online privacy while exploring the depths of the internet. The dark web has gained notoriety in recent years, becoming synonymous with hidden marketplaces, cybercriminal activities, and anonymous browsing. It is a part of the internet that is not indexed by search engines and can only be accessed through specific software and configurations.
- Traders cash in on stolen credit card data dumps, initial access points to vulnerable systems, credentials, and intellectual property belonging to companies compromised during cyberattacks.
- It is specifically designed to make hidden services on the Tor network more accessible.
- Again, people who live in countries where the freedom of the internet is limited, for example in China, can really benefit from using Tor.
- Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there.
- So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers.
- Many dark websites are perfectly legal and safe to use and, in many cases, are better for your privacy than clear websites.
Tor-Enabled OS Alternatives To Tails For Secure Dark Web Browsing
As the name suggests, Dread is a hidden internet forum designed to look like the legitimate website Reddit – it’s easy to say that it’s the dark web Reddit. It was created in 2018 and has gained popularity with hundreds of posts a day at the moment. It is a forum on the darknet that’s designed like X (formerly Twitter). Like a lot of other forums in a similar domain, Pitch is significantly focused on corporate access, hacking, and data leaks, making it a communication hub where hackers and cybercriminals gather. The tor expert bundle contains the tor and pluggable transports binaries, bridge strings, and geoip data used in Tor Browser. The two versions shown indicate the version of Tor Browser these particular binaries were built for and the version of the contained tor daemon.
Verify All onion Links
It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows. A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want.
Ways Small To Midsize Businesses Can Stay Safe In The Cloud
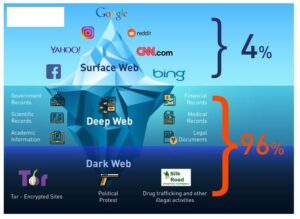
Additionally, many Internet Service Providers (ISPs) flag Tor usage as suspicious and may block access to the network altogether. The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives. We strongly advise you against visiting it, even if your intentions are good. Contrary to a widespread misconception, the dark web is a tiny part of the web. According to Recorded Future research1, out of 55,000 onion domains discovered, only 8,400 have a live site. Though the dark web offers anonymity for journalists and activists in oppressive regimes, it raises many ethical concerns.
Fake sites are everywhere, and even a one-character difference in the URL can land you on a phishing page. Never install extensions or additional add-ons, even if they seem useful. They change your browser fingerprint and make you easier to track. The Hidden Wiki is a popular onion link directory on the dark web offering categorized lists of sites.
Security-focused Operating Systems
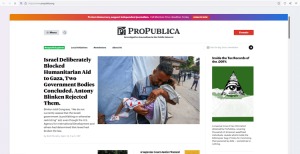
The Tor Browser is a popular online anonymity tool among political activists and journalists who fear totalitarian governments monitoring or arresting them. Other users appreciate the browser as it allows them to circumvent censorship. And yes, unfortunately, those seeking to perform criminal acts also use it. When you use the Tor network, your traffic is layered in encryption and routed via a random relay, where it’s wrapped in another layer of encryption. For example, legitimate sites, such as the BBC, the New York Times, ProPublica, and Facebook, have made their sites accessible as a Tor Onion URL to help people avoid government censorship. These sites are only accessible over the Tor network and are commonly used for privacy and anonymity.

Can Tor Browser Be Used For Regular Internet Browsing?
In fact, there have been instances where attackers controlled hundreds of Tor nodes. This process anonymizes your browsing not only to websites but also to your internet service provider and anyone trying to monitor your network traffic. The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security.
Method II – VPN Over Tor
- You can download the Tor Browser for Windows, MacOS, Linux, and Android.
- However, its network is still small, and there aren’t many hidden services available yet.
- To get on the dark web, you need a browser built for the job, and the best in the business is Tor.
- Tor has an in-build slider which lets you adjust the level of security.
- Otherwise, you risk downloading fake apps that might infect your device with malware.
- A secure VPN server slows down your browsing much less than the Tor Browser and also opens access to geo-blocked local content around the globe.
To do so, enter a .onion URL and you’ll be taken to the dark web page being served at that address. A large portion of activities on the dark web involve illegal content, transactions, or services. Simply accessing certain sites or engaging with the wrong links could implicate you in criminal investigations. While Tor offers anonymity by routing your traffic through a decentralized network of nodes (onion routing), it shouldn’t be your only line of defense for privacy. Malicious actors and government agencies can run Tor nodes, compromising privacy and security.
In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. In opennet mode, the network will automatically assign you to other users on Freenet’s network. It’s impossible to access the dark web with a regular browser like Chrome or Safari.
What Is The Dark Web? Here’s Everything To Know Before You Access It
The Tor Network consists of many relays that bounce your communications around so many times that it prevents site owners and networks from knowing your real identity. This wikiHow guide will teach you how to set up and connect to the Tor network on any device—even if your school, work, or network blocks Tor downloads. In this article, we have explored what the dark web is and how Tor Browser provides the necessary anonymity and encryption to access it. We discussed the importance of setting up Tor Browser correctly, ensuring security and anonymity, and navigating the dark web safely.
Can I Use Tor Browser Without Installing It?
The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily. When you search for something on Google or Bing, you’re using the clear web. Simply accessing the dark web and using the Tor browser may already raise government suspicion. Tails is a mere 1.3 GB download, so on most connections it will download quickly. You can install it on any USB stick that has at least 8 GB of space. Keep in mind what you’re looking for, find that information, and disconnect from the dark web.
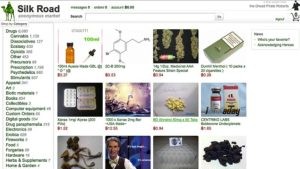
The rise of cryptocurrency, and in particular Bitcoin, significantly increased the dark web’s use in illegal trade. Users could exchange funds online without sharing credit card numbers or other identifying information. In February 2011 Ross Ulbricht founded what is believed to be the dark web’s first black market, Silk Road. The U.S. Federal Bureau of Investigation (FBI) arrested Ulbricht in October 2013, but imitators still arise, many much larger. Analytics Insight is an award-winning tech news publication that delivers in-depth insights into the major technology trends that impact the markets. The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation.
A premium user has access to the private Telegram channels that include an exclusive leak channel that’s unavailable to regular members. Its popularity can be as a result to the ease of use on it, as the forum features a clean and accessible design with enhanced moderation and a wider scope of the leak topics and sources. BreachForums made its name as one of the top forums for leaked databases as well as stolen credentials immediately after RaidForums was closed down. It’s a well-known forum for strong escrow services, a repository of more than 15 billion records, and a VIP ranking system that makes it a top player. Its decentralized community structure makes it one of the best forums, and its security measures help it to withstand threats like DDoS attacks. Ideally, the forum operates within the Tot network, enhancing user anonymity.
By distributing communication over several nodes, it obscures the user’s IP address. Indeed, most nations; including the United States, the United Kingdom, and India, allow access to the dark web as a lawful activity. Exploring the dark web can be eye-opening, but it’s also risky without the right protection.