Accidental leaks at the Tor entry nodes can potentially expose your IP address. Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. If you are in a position to report the incident safely, you should report it to the authorities immediately. It’s recommended not to be too vigilant here and leave the investigation to the professionals. Some services are genuine; you can get what you want at an agreed fee.
Exposure To Illegal Content
- The Tor Browser, as we know it, is available for Windows, macOS, Linux, and Android.
- This benefit is particularly valuable for researchers exploring the invisible web, as it simplifies the communication of findings.
- By being aware of the risks and implementing best practices, you can navigate the Dark Web more securely and responsibly.
- For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship.
- It indexes a wide array of content, including both legal and illegal sites.
- Another factor to consider is that many Dark Web websites are intentionally hidden and require users to have specific URLs or addresses to access them.
To get the full potential of SearXNG, especially for deep web content, use the Tor browser. This combination increases your chances of finding concealed or hard-to-find information while maintaining high privacy. In 2025, watch VormWeb for its safety ratings on results and Tordex for enhanced multilingual crawling, both building on trends like AI moderation.
What Happens If You Go On The Dark Web Without A VPN?
Fazzle is a versatile metasearch engine that combines the power of various search tools to provide complete searches, bringing together a wide range of information in one place. It is particularly helpful for people who need to search through multiple sources without having to jump from one search engine to another. In 2025, as privacy battles intensify, these tools are more vital than ever. Fire up Tor, choose your engine, verify your .onion links, and dive in—just keep your digital armor on.
How To Stay Anonymous On The Internet In 2025
A reputable provider ensures that you can explore the invisible web without unnecessary risks. This search engine excels at indexing a wide range of content, including forums, marketplaces, and academic resources. Its advanced algorithms deliver accurate search results, helping you locate relevant information quickly. LibreY is particularly useful for research purposes, as it provides access to resources often overlooked by other deep search engines.
How To Find New, Active Dark Web Links
The search engine excels at indexing a wide range of content, from forums to marketplaces. Its advanced algorithms deliver accurate search results, helping you find relevant information quickly. NotEvil is particularly useful for research purposes, as it provides access to resources that are often overlooked by other deep search engines. The search engine delivers accurate search results by focusing on indexing legitimate hidden services. Whether you’re conducting research or searching hidden services, Ahmia provides a reliable platform for uncovering valuable information.
Words Of Caution When Using Dark Web Sites
It became the dark web’s de facto entry point, akin to a digital yellow pages, but its manual curation limited scalability. NotEvil, a successor to TorSearch, is a dark web search engine launched in the mid-2010s, designed to index .onion sites with a focus on privacy and safety. Its name is a nod to Google’s former motto, “Don’t be evil,” positioning it as a moral alternative to unfiltered engines like Torch.
In conclusion, while the dark web holds many secrets, accessing it safely and securely is possible with the right tools and knowledge. With Forest VPN, you can explore this hidden part of the internet without compromising your privacy or security. Discover how to safely use a dark web search engine for exploring the hidden internet.
Find The onion Address You Want To Access

One thing to be cautious about is that Torch does not censor pages, just like the majority of dark web search engines. This raises the possibility of coming across dangerous content or a rogue website. While the Tor network was not created for illegal activities, as it’s harder to trace websites to their physical location, cybercriminals have also adopted it to host their websites. The Tor Browser is an open-source web browser created for anonymous browsing and to evade censorship. It routes users’ traffic through thousands of volunteer-run servers called nodes/relays.
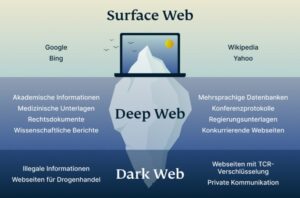
Aimed at giving users a better understanding of government service, it’s a valuable resource for citizens seeking government-related information. In this World Wide Web layer, there are password-protected websites, proprietary databases, confidential academic research, and much more that are usually not indexed by common search engines. Haystak Haystack is a unique dark web search engine that stands out due to its extensive index of uncensored .onion sites. Committed to user privacy, it employs robust protections, ensuring your searches remain confidential. Dark web search engines are the gatekeepers to the Tor network’s hidden corners, empowering users to explore what’s intentionally unindexed.

Although the Tor browser protects your online privacy using a reliable VPN at the same time is a plus. A VPN will encrypt your traffic and hide your IP address, making it much harder for someone to track you down. Additionally, if you are on a clear net, a VPN will give you access to blocked websites and content. According to my personal experience, Deep Search seems to provide pretty accurate and useful results, unlike others who spam users with spam links. Another noteworthy feature of Deep Search is that it provides a list of marketplaces, exchanges, and websites involved in scamming users.
Accessing The Dark Web: A Step-by-Step Guide
It aims to serve as a database through which users can search for products from different vendors in different marketplaces on the dark web. The Tor network consists of a series of volunteer-run servers that route internet traffic through a series of encrypted tunnels. This makes it difficult for anyone to track your online activity or identify your location. It is worth noting that for clearweb, web browsers like Brave and Antidetect browser

Ahmia is one of the search engines designed to be accessed on the Tor browser. It’s widely used by people on that browser, but you can also use it on regular browsers as a privacy-focused search engine alternative to Google. It will give you more results than you’ll find on Google and doesn’t order or filter what you find based on advertising. For most Internet users, the online world begins and ends with Google.com.

These experiences taught me to use Tails OS, verify links, and stick to filtered engines for sensitive work. However, privacy risks (e.g., AI tracking, regulatory overreach) demand vigilance. Staying updated via r/onions, tor.taxi, or security blogs will be crucial to leverage these advancements safely. By 2027, engines could optimize for 5G-enabled Tor browsing, offering image-heavy results or real-time updates. Accessibility features (e.g., screen reader support) may emerge, making the dark web inclusive for visually impaired users, though bandwidth constraints pose challenges.
First and foremost, you want a search engine that is private and secure, as well as one that can be used anonymously. ThreatMon’s Deep/dark web monitoring service provides proactive identification and monitoring of compromised corporate data, sensitive information, or credentials on the dark web. Threat Intelligence roams the dark web, analyzes criminal activity, and gathers clues for its purpose. It monitors dark web forums and marketplaces related and monitors postings.

Check around with other users and ask if they know anything about the new marketplace. There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web. Simply download the file, install the software, and you’re ready to use its web-based interface. I2P can only be used to access hidden sites that are only available on the I2P network.