It encompasses public domains such as websites, social media platforms, news sites, and online stores—content accessible to anyone with the help of the internet and a web browser. Many people use Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities. Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites. The dark web — aka, the deep web — is the second layer of the internet, which is not indexed by search engines.
A Dark Web Search Engine
Though you likely won’t remember the addresses of onion websites, you can find these URLs on various websites on the internet. Check onion links through trusted directories, user reviews, and reputation checks. Use directories like The Hidden Wiki or Dark.fail, which list verified and regularly updated onion links.
This makes it extremely difficult to find out who you are transacting with. ZeroBin is a wonderful way to share the content you get from dark web resources. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee. In most cases, whistleblowers have sensitive information about the government or a company. They can be easily traced and even prosecuted if they share the information on the surface web.

Step-by-Step Guide
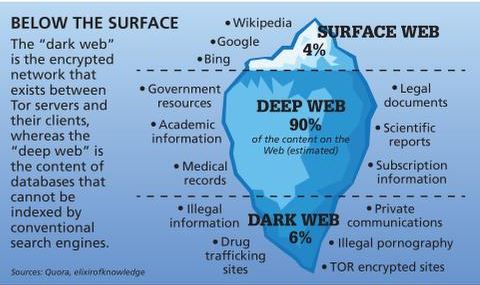
You just need standard browsers like Chrome, Edge, and Safari to open websites on the surface web. Stolen information from data breaches, drugs, guns, malware and various other illegal items can be bought there. Check out our article on the dark side of the dark web for more information about the dangers of the darknet. If you’ve already done that, or even something similar, that’s good news – you’re already a deep web user accessing information not available through common search engines. Everything from social media data to medical records are held on the deep web, as is all your email information.

Connection speeds are very fast, and you should be able to stream HD and 4K content without buffering. Surfshark works well with streaming platforms and is able to access geo-restricted content from the likes of Netflix, HBO, Hulu, and Disney+. Authorities infiltrate dark web marketplaces to gather evidence and track down criminals. One of the darkest aspects of the dark web involves human trafficking, illegal pornography, and other forms of exploitation.
Tor Over VPN Vs VPN Over Tor: Which Should You Use?

A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. You should never use your personal information on the dark web anywhere else in your life. In fact, create new throwaway accounts and documents if possible.
Tor And Onion Routing Explained
It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections. However, using Tor has some challenges that you should be prepared for. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic. Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it.
Onion Links: How To Access Them

Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data. In 2002 the dark web began to grow significantly when researchers backed by the U.S. Journalists in overly restrictive countries also appreciate the anonymity of the dark web.
Install And Update Security Software
You can install it on any USB stick that has at least 8 GB of space. Keep in mind what you’re looking for, find that information, and disconnect from the dark web. As enticing as it might be, don’t follow links to other parts of the dark web. Check around with other users and ask if they know anything about the new marketplace.
In this instance, too, it is important to use a logless VPN and pay with Bitcoin if you can to stay anonymous. The VPN over Tor technique is also susceptible to an end-to-end timing attack, though it’s highly unlikely. Always exercise extreme caution when using publicly posted onion URLs. If you can’t get a personal recommendation from someone you trust, verify the URL from multiple sources. Our rigorous research and testing have revealed revealing truths and busted myths. We’ll navigate this intricate maze with you, uncovering its secrets while ensuring your online safety.
Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Users who wish to gain access to such information are protected by the same anonymity the publishers of the content enjoy. Well-known news websites, such as ProPublica, have launched deep websites. Meanwhile, Facebook also offers dark web access to their social network. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers.
- Deep web content includes academic research papers, court documents, or medical records.
- The Dark Web can provide a platform for individuals to share information, documents, or evidence anonymously, ensuring protection against potential retaliation.
- The dark web is a dangerous place, and all bets are off on your safety.
- In addition, it uses a distributed network database which is harder to attack than Tor’s fixed, trusted Directory servers.
- It connects you to a network of servers rather than a particular server.
FAQs On Accessing The Dark Web Safely
- Dark web websites don’t bear Internet Corporation for Assigned Names and Numbers (ICANN) domains, such as .com.
- Since their deadline wasn’t met for the closer of the sites a month later, the Impact team ascended to the dark web, where they started to publish the data.
- Generally, it’s important to use Tor responsibly and in accordance with local laws and regulations.
- ZDNET tested the best VPNs available based on speed, number of servers, security features, price, and more.
- The anonymous nature of the Dark Web makes it challenging for law enforcement agencies to track and prevent the flow of illegal weapons.
The Dark Web’s anonymity and encrypted transactions make it an appealing platform for drug traffickers and buyers seeking discretion. The dark web intelligence market experiences a dynamic increase in cybercriminal operations. 4iQ reported that stolen account credentials on the dark web experienced an 82% increase in 2022 to reach 15 billion. The deep web is significantly larger than the surface web, but it’s not inherently illicit or dangerous. In fact, most of the deep web consists of perfectly legal and functional services that are simply not meant for public access.



