
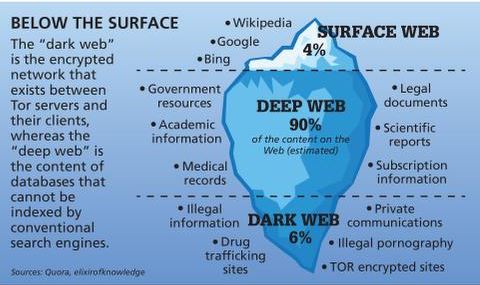
Tor routes your traffic through a chain of relays to obscure your IP address. This makes it harder for websites, ISPs, or surveillance tools to see who you are or what you’re doing. Many sites on the dark web are scams, and some host illegal content. The deep web refers to anything that search engines can’t crawl.1 These pages aren’t public — not because they’re illegal, but because they require a login or special access.
Onion Routing And Tor Network
It offers better speed and security than other alternative methods. The Deep Web includes unindexed content like private databases and password-protected sites accessible with standard browsers. The dark web marketplaces thrive on the demand for illegal services and extreme content.
Is Accessing The Dark Web Illegal In India?
The Tor network combined with a VPN is one of the safest ways to get on the dark web. Many internet service providers (ISPs) and governments are suspicious of Tor use, but a VPN will hide your internet activity and help prevent anyone from knowing that you’re using Tor. Everything else on the internet is located on either the deep web or the dark web – and they aren’t as easily accessible, or as safe. So if you’re planning on accessing the dark web, here’s all you need to know to access it safely. However, using the dark web for illegal activity can be a criminal offense.

How To Watch The Google IO 2025 Keynote
Tor shares similarities with VPNs and proxy servers — all of these tools allow anonymous browsing. Tor can be used together with a VPN to provide overlapping layers of privacy and anonymity. The difference between the dark web and the deep web is that the deep web refers to websites and web pages that aren’t indexed by search engines, like login pages and payment portals.

Major Risks And Downsides
Hacked data, credit card details, and personal information are frequently traded on the dark web. Illegal marketplaces like the now-defunct Silk Road have facilitated drug sales, arms trading, and other prohibited activities. Pushing your hardware to its full potential — such as by enabling XMP — ensures that you get the best performance which is crucial for all sorts of heavy tasks including gaming. Memory is one of the key components that can bring a noticeable improvement in video quality and speed. While visiting any of the sites you find on those Wiki sites, do not maximize your browser, as it can help identify you by your monitor resolution. It offers outstanding privacy features and is currently available at a discounted rate.
Don’t Buy Anything
In other words, these are pages that aren’t indexed and therefore can’t be found by a typical search engine. A step-by-step guide to safely accessing the dark web while maintaining your anonymity and security. However, note that a VPN is not a definitive or comprehensive form of protection. It won’t guard you against all of the many threats that exist on the dark web, from phishing scams to malware and malicious sites.
Dark Web Tools & Services
- There are multiple search engines on the dark web that can help you find what you’re looking for.
- It is a subset of the Deep Web, which includes any web content that is not indexed by search engines.
- Stay updated on the latest practices for securely transacting with cryptocurrencies.
- Also, you can set a strong password to protect your message and choose how long it will take to expire.
- Cryptocurrency activities, discussions and communities, and even academic resources further populate this hidden corner of the internet.
Unlike other search engines, it does not collect or share web activities and personal data of users. The reputation of the dark web has often been linked to criminal intent or illegal content, and “trading” sites where users can purchase illicit goods or services. Yes, governments and law enforcement agencies have developed sophisticated techniques to track and investigate illegal activities on the dark web. They can sometimes identify users through other methods, such as monitoring behavior, exploiting vulnerabilities or conducting undercover operations. Browsing the dark web safely requires more than just Tor — your ISP can still see you’re using it.
How To Access The Dark Web Using TOR Browser?
You can still be tracked at network entry and exit nodes, as indicated by reports that police identified Tor users by surveilling data centers. Consider turning on your VPN at this stage in the preparation process. The VPN connection will route your online activity through a different server, masking your activity from your internet service provider.
For example, randomly clicking a link can land you in extreme content, such as child pornography, which is a serious criminal offense to access. Threat actors also exploit vulnerabilities in your systems and software to gain access to them. So, you should also make sure that your system’s operating system and other installed software are patched with the latest updates. So, you should never share your personal information on the dark web. What’s more, they can also sell you personal information on the dark web as your personal data has a monetary value on the dark web. The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives.
To reduce the risk of these threats, it’s highly recommended to disable JavaScript when browsing dark web sites. The Open Web, also known as the surface web, constitutes the most accessible layer of the internet, readily navigated through popular search engines like Firefox, Google, Bing, and Yahoo. It encompasses public domains such as websites, social media platforms, news sites, and online stores—content accessible to anyone with the help of the internet and a web browser. If you log into personal accounts on the dark web or visit websites with tracking scripts, then your activity may be tracked. Similarly, unless you’re using a VPN, your IP address will be visible to the first relay node you connect to. Unlike typical web browsers, Tor Browser uses onion routing, which encrypts and routes traffic through multiple servers around the world to hide your IP address and provide private browsing.
These are platforms where leaked or stolen data, including personal information, passwords, and credit card details, are bought and sold. They often provide access to vast amounts of compromised data from previous hacks or breaches. Cybercriminals often disguise malware within legitimate-looking files to trick users into compromising their own security. Once downloaded and opened, these files can install viruses, spyware, ransomware, or other harmful software without your knowledge. However, with the right security measures and cautious browsing, you can minimize these dangers. The dark web, a subset of the deep web, cannot be accessed with a regular browser.
- In this instance, too, it is important to use a logless VPN and pay with Bitcoin if you can to stay anonymous.
- While the process is not overly complicated, it demands attention to detail, adherence to best practices, and an understanding of the risks.
- Furthermore, it’s critical to understand that Whonix is not a stand-alone browser.
- Engaging in such activities is a criminal offense and can result in severe legal consequences.
- In due course, the framework was remodeled and made public as a secure browser.
- In this way, your browsing experience is made as anonymous as possible – if someone was ‘watching’ you, so to speak, all they’d be able to see is that you’re using Tor.
However, you can check out this guide for the best ad blockers to avoid annoying ads. On top of that, the provider offers perfect forward secrecy (PFS). A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. It is imperative to stay alert and trust your gut when on the web. You should never use your personal information on the dark web anywhere else in your life. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web.



