
The dark web is a common gathering place for hackers and other cybercriminals, which can make browsing the dark web a risky activity. Visitors to the dark web should exercise extreme caution when downloading files, as they may infect your devices with viruses, malware, trojans, ransomware, or other malicious files. At a minimum, users should ensure that their cybersecurity defenses are activated and up to date.
How Do I Access The Dark Web Safely Using Tor Browser?

Understanding the history of the Dark Web provides valuable insights into its origins, development, and the challenges it poses for cybersecurity professionals. By studying its past, we can better prepare for the future and develop effective strategies to navigate and secure this hidden part of the internet. VPNs are also used for accessing geo-locked content hosted by streaming services.
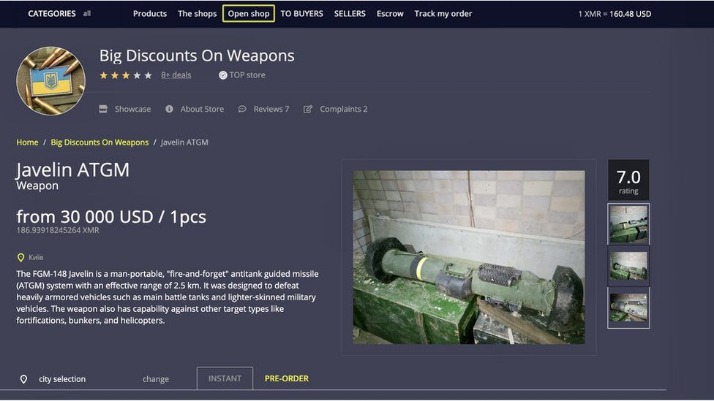
The dark web is a part of the internet that isn’t indexed by search engines. You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is. Researchers Daniel Moore and Thomas Rid of King’s College in London classified the contents of 2,723 live dark web sites over a five-week period in 2015 and found that 57% host illicit material. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites.
While the Dark Web remains a core venue for privacy-seeking users and covert activities, a range of emerging platforms and shifting trends shape the broader ecosystem of underground communication. Remember that good judgment, ongoing education, and constant vigilance are your most powerful tools for maintaining a safe and private Dark Web experience. Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web. While the process is not overly complicated, it demands attention to detail, adherence to best practices, and an understanding of the risks.
In-Depth Guide On How To Download Instagram Videos Beginner-Friendly
By following these guidelines, you can minimize the potential risks and protect your online privacy while exploring the depths of the internet. The most popular misunderstandings regarding the Regular Internet is that it is compatible with the Deep Web. While ordinary search engines do not index both, users must grasp the difference among the two. The Deep Web refers to any material that is not searchable, such as online banking and email, premium service services, and academic databases. The Dark Web, on the other hand, is a small fraction of the Deep Web that is purposefully concealed and can only be accessed with specialist software such as Tor.
What Is Dark Web Link : How To Access onion And Tor Sites Safely In 2025
Cybercrime services, such as hacking tools and stolen databases, are available for hire, creating a marketplace for illicit online activities. Dark web monitoring platforms provide secure communication channels for individuals seeking to expose information without fear of retribution. Additionally, the Dark Web serves as a haven for those in censored environments, offering access to restricted information and enabling the free expression of opinions.

It will still be able to get the job done if you’re interested in dark web browsing. As the digital world continues to evolve, the Dark Web will undoubtedly remain an important and often controversial part of the internet’s landscape. Whether used for good or ill, its shadowy nature is unlikely to fade anytime soon. Finally, Tor’s encryption system is quite complex, meaning it can be a very slow process to navigate from A to B across the web.
Minimize Or Rescale Your Tor Browsing Window

I’ve put together detailed guides on how to access the dark web safely on both Android and iOS. I also share essential tips for staying secure there — personally, I always use a VPN for added privacy since Tor isn’t completely secure on its own. By being aware of the potential risks, following recommended security practices, and using the Dark Web responsibly, you can navigate this hidden part of the internet more safely and effectively.
Invest In A VPN
This node decrypts your traffic and it reaches the destination i.e. the website you want to visit. This is usually done to prevent tracking and website shutdowns typical for this part of the internet. The trick with these onion websites is their accessibility, which is made possible only with Tor. Tor over VPN directs your traffic through the VPN server before going through Tor’s network — while VPN over Tor directs your traffic through Tor’s browser first.
Security Links
The same general process applies to other operating systems, as Tor is also available for Mac and Linux. We test each product thoroughly and give high marks to only the very best. We are independently owned and the opinions expressed here are our own.
You can access the dark web on mobile with a dedicated dark web browser app. Install a mobile dark web browsing app — like Tor browser for Android or the Onion browser for iPhone — and enter an onion URL to start browsing. Encrypting your communications is crucial when navigating the Dark Web. By encrypting your messages, you can ensure that only the intended recipient can read them, protecting your privacy and preventing unauthorized access.
IBM Security X-Force, for example, reported that 29% of its ransomware engagements in 2020 involved REvil. The criminal groups that developed the malware gets a cut of the affiliates’ earnings, typically between 20% and 30%. A study, Into the Web of Profit, conducted by Dr. Michael McGuires at the University of Surrey, shows that things have become worse. The number of dark web listings that could harm an enterprise has risen by 20% from 2016 to 2019.

VPN over Tor means you connect to the Tor network first, and then your traffic goes through a VPN. Be cautious of random or obscure links — these could lead to dangerous or malicious websites. If you’re unsure about a link, do some research or ask trusted sources within dark web communities. A good antivirus software can detect, quarantine, and remove threats before they can damage your device or acquire any sensitive information.
Onion websites are websites that are only accessible through the Tor network. The “.onion” extension signifies that the website is hosted on the Dark Web and relies on the Tor network’s encryption and anonymity features to protect user identities. When accessing the Dark Web, you will encounter websites with addresses that end in “.onion”. These unique URLs are specific to the Dark Web and cannot be accessed through regular web browsers. Understanding how onion websites function will help you navigate the Dark Web more effectively and safely.
- Be sure to only download it from the official site to avoid fake or malicious versions.
- Using a privacy-focused operating system adds an extra layer of security when accessing the dark web.
- The dark web is a small, hidden subset of the deep web that requires special tools to access.
- The easiest way to access Tor is through a special browser known as the Tor Browser.
- A lot of illegal activity takes place on the dark web, and engaging in any of that activity can be a criminal offense.
The Tor browser is the most popular tool, though you can also use Freenet, ZeroNet, I2P, and Riffle. Proton VPN makes it easy to safely gain access to the dark web by connecting users to the Tor Network in a single click. Its server network includes dedicated nodes set up to reroute internet traffic through the Tor network.



