Taking these proactive steps will fortify your defenses against potential dangers lurking on the dark web. Sanctioned nations use cryptocurrencies to evade economic restrictions, conducting cross-border transactions and mining digital assets to generate revenue. The decentralized nature of crypto complicates enforcement, prompting governments to develop advanced tracking strategies. Emerging threats include the use of stablecoins for financial stability and privacy coins for anonymity. Authorities are strengthening forensic blockchain analysis and regulatory measures to counter crypto-enabled illicit financing while balancing financial innovation.
The Importance Of Staying Anonymous
Anyone who stole a Bitcoin address’s secret key could empty out that address like a digital safe. Unlike with credit cards or other digital payment systems, there was no overseer who could stop or reverse the money’s movement. The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously.
This makes it difficult for individuals to recover funds if they fall victim to fraudulent schemes. While investigating cryptocurrency-related crimes can be complex, it is not impossible. Silk Road was utilised by its users as a black market for all types of (in most countries) illegal activities, like buying and selling drugs, credit card data or even guns and other weapons. It was the first Darknet black market of its kind and was the precursor for many similar sites. Firstly, you may encounter scammers who pose as legitimate sellers but never deliver the promised goods or services. Secondly, there is a risk of law enforcement agencies tracking your Bitcoin transactions and linking them to illegal activities.
What Is A Dark Wallet?
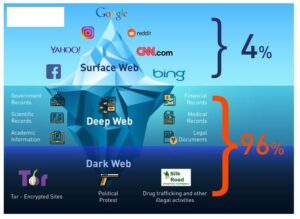
Within the realm of cryptocurrencies, the Dark Web has become a platform for people involved in crypto to engage in transactions and exchange information. In particular, Bitcoin is commonly used for illegal activities such as drug trafficking and money laundering on dark web marketplaces such as the infamous Silk Road. These marketplaces allow buyers and sellers to conduct anonymous transactions using Bitcoin.
Alleged Owner Of Darknet Narcotics Bazaar ‘Incognito Market’ Arrested In New York

In Satoshi Nakamoto’s own original white paper, Meiklejohn recalled that he had briefly alluded to a technique that could be used to collapse some addresses into single identities. Often, a single bitcoin transaction has multiple “inputs” from different addresses. To make the payment possible, the payer would need to possess both of the so-called secret keys that allow the five coins at each address to be spent. That means anyone looking at the transaction on the blockchain can reasonably identify both of the input addresses as belonging to the same person or organization.
The dark web offers a level of anonymity that is not available on traditional online platforms. Users can conduct transactions without revealing their identities or personal information. This privacy makes it attractive for illegal activities such as buying and selling drugs, weapons, and stolen data. Bitcoin’s anonymity and the lack of a centralized authority make it an attractive tool for money launderers. The dark web is a hidden network of websites that can only be accessed using special software.
Data Availability

The dark web, with its emphasis on privacy and anonymity, has become a breeding ground for various scams and fraudulent activities involving Bitcoin and other cryptocurrencies. These activities take advantage of the decentralized nature of the blockchain technology that powers cryptocurrencies, making it difficult to trace and recover stolen funds. On the other hand, Bitcoin tumblers can facilitate illegal activities, as they make it difficult for law enforcement agencies to track down criminals and gather evidence. This has led to increased scrutiny from regulatory bodies and governments, with some countries banning the use of Bitcoin tumblers altogether. The decentralized nature of cryptocurrencies also enables ransomware attacks, another form of cryptocurrency crime. Ransomware is a type of malware that encrypts a victim’s files and demands a ransom, typically in Bitcoin, in exchange for the decryption key.
What Risks Are Associated With Buying Bitcoin Anonymously?
Furthermore, data will help to detect attacks against the network and possible censorship events. This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. Even without monitoring your browsing activities, DuckDuckGo will offer decent answers to your questions.
Accessing Onion Sites On Android
The use of Bitcoin in legal transactions is a testament to its legitimacy as a currency. In 2015, after refusing a plea deal, Ulbricht was convicted and sentenced to life imprisonment without the possibility of parole. He was charged with money laundering, computer hacking and trafficking fraudulent ID documents, as well as allegedly paying to have two people murdered and other narcotics charges.
These undertakings range from assisting individuals with finding a dress online to offering educated specialized responses to their inquiries. The absolute most punctual excavators had the option to mine many BTC using only their Home Computers. To mine in the present BTC scene, you’ll need top-level hardware, which can slow down you two or three thousand bucks. Likewise, since Bitcoin has become famous now, you’ll have a ton of rivalry. You will find many more dark web wallets and also bitcoin mixers on the clear web, but most should be avoided since they are unproven and might not make your bitcoin anonymous.

Hence, the need to buy Bitcoin anonymously becomes crucial for those seeking true privacy. However, Dark Wallet only recorded one transaction by joining them together. The ledger would show that bitcoins were paid from the addresses of A, C, and E to those of B, D, and F. By masking the deals made by all parties, a tracker could not determine with certainty who sent bitcoins to whom. Coin mixing was also done when a user transferred coins from one pocket to another. This feature reduced traceability by mixing or combining a user’s transactions with those of random users who happened to be making transactions at the same time.
Ponzi And Pyramid Schemes In The Digital Era
- One of the primary reasons why Bitcoin became popular on the dark web is its inherent nature of allowing users to transact without revealing their identities.
- We have not found any additional information, such as a review, which contains more than what is on the BG site.
- Particularly, the first online dark web marketplace, the Silk Road, relied heavily on Bitcoin as an alternative to conventional and highly-censored payment systems.
- On one hand, it enables individuals to protect themselves and their privacy.
- However, it fills a rewarding criminal subculture that could threaten businesses and customers.
- The empty point on the multiseller median income line demarcates the quarter with only two multisellers.
While Bitcoin provides a certain level of anonymity, it is not completely untraceable. Bitcoin transactions are recorded on the blockchain, a public ledger that allows anyone to view the transaction history. Law enforcement agencies and other entities with the necessary resources can analyze the blockchain to identify and track users involved in illegal activities on the dark web. The dark web operates on the principle of anonymity, where users can engage in illicit activities without revealing their real identities.
Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links. Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile. Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol. It assigns a task to the client instead of the server, eliminating server-related vulnerability.
The vendors aren’t required to register or apply for a vendor account while using this platform. It ensures the buyer’s identity is kept hidden and accepts payments through cryptocurrencies, including Bitcoin, Litecoin, Ethereum, and Monero. However, the website has some security risks, and users experience glitches. The marketplace has a pleasant, user-friendly interface built from the ground up. Its interface makes it easy to identify clone websites and ensures that users always use the authentic site. The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption.
Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together. Formerly known as Archive.is, it is one of the best onion sites on the dark web. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network.