Smarthistory’s free, award-winning digital content unlocks the expertise of hundreds of leading scholars, making the history of art accessible and engaging to more people, in more places, than any other publisher. As discussed at the beginning, the fact that race no longer feels peripheral on the internet is a dramatic change from the years when the Black.Net.Art Actions were being produced. In the 1990s and early 2000s, the myth that race disappears online still shaped how many people understood the emancipatory potential of computer networks. The Actions helped to counter that myth by revealing how the histories that influence our ideas and experiences of race persist throughout our encounters on the network. In the process, these artworks also demonstrated that the relationship between race and computer networks is an essential subject for internet-based art. During this same period internet art, or net art, was becoming a more widely recognized category of artistic practice.
Crawlers can automatically scan websites and their links, then record them. In order to understand the dark web properly, you need to understand that the internet is a huge and sometimes disorganized place. It has billions of sites and addresses, it is amazing that we can both search for – and find – anything. What should you do if your information is found in a data breach or you think it’s been leaked somewhere?
- Surface web search engines can’t access the darknet, but specialized dark web search engines can help you find what you’re looking for.
- I think the fullest form of understanding that can exist between two people is knowing that no such thing actually exists.
- Many of this generation’s most important social movements were birthed on Black Twitter, including #BlackLivesMatter, #OscarsSoWhite, #SayHerName and the #MeToo movement.
- Without Black people coming to urban centers up north like Chicago, Detroit, and New York, we wouldn’t have any of the contemporary Black culture we have today.
- If you have a legitimate or viable need to access the dark web, you’ll want to make sure you stay safe if you decide to use it.
- There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game.
Black-Owned Technology Platforms Building Digital Communities
The dark web is infamous as a dangerous place, where drugs are bought and hitmen hired, but it can be a safe way to browse the internet if your privacy is serious concern. If you choose to pursue exploring any sites on the dark web, you put yourself at risk of being singled out and targeted for hacks and more. Most malware infections can be caught by your endpoint security programs. Sites on the deep web also use Tor (or similar software such as I2P, the “Invisible Internet Project”) to remain anonymous, meaning you won’t be able to find out who’s running them or where they’re being hosted. Understanding that the nature of the internet meant a lack of privacy, an early version of Tor was created to hide spy communications. Eventually, the framework was repurposed and has since been made public in the form of the browser we know today.

More On Tor Onions
Popcom, also known as Solutions Vending International, develops software for hardware to advance the automated retail sector. The company’s automated retail technology platform provides business owners and brands with retail solutions that are geared for the future and enable rapid retail development, fantastic customer experiences, and valuable sales data. In the case of Riley, Washington, and Turner, the federal government says each location is served, despite slow speeds.
Tips For Safe Access To The Dark Web
She accesses the internet through a laptop at home but pays more than $100 for her internet plan. All her college classes require internet access and her children rely on it to complete their school work as well. Amanda is studying child development at Fresno City College and hopes to transfer to Fresno State in the fall. Daisy is a 17-year-old Latina Fresno resident (ZIP code 93706), a high school senior who lives with her parents and two brothers on a $1,600 monthly income. She accesses the internet through her phone and uses it to complete homework. Each day she spends about an hour doing homework, but estimates that if she had home internet and a computer it would take her half that time.
What Is The Dark Web? How To Use Tor To Access The Dark Web
Disparities in technology and internet access have always been prevalent. Efforts must address poverty, geographic and social isolation, and digital equity, which is a requirement with BEAD. Philadelphia, Mississippi, is 54% Black, and and the median income is $37,000. A Brookings Institution study showed that the less money an individual makes, the more likely they won’t have access to high-speed broadband. Given the history of neglect to Black communities, residents in rural Alabama, Georgia, and Mississippi told Capital B they question whether the billions of dollars from the feds for broadband will reach their area. It became difficult for some residents to pay a bill online, complete school work, and access unemployment benefits or banking services.
What Is The Dark Web And How Do You Access It?
The Tor browser can conceal your true location by shunting your traffic through various relays. But it can’t stop you from entering personal information on websites to say where you are. Your connection also may be encrypted but if you do something like send an email from your personal account, then anyone with access to your inbox will know that you were online at that time. It’s also used by political activists and dissidents, journalists, people who don’t trust websites’ use of their personal data, and the odd member of the tin foil hat brigade, convinced the government is spying on them at all times. Deep sites also include company intranets and governmental websites, for instance the website of the European Union. You may be able to search such pages but you do so using their own internal search function, not a search engine like Bing or Yahoo.

The president said his administration planned to send 1 million COVID-19 vaccine doses a week to community health centers in the “toughest neighborhoods in terms of illness” as well as over 6,700 pharmacies. Levy asked whether lessening the impact of COVID-19 on Black and Hispanic communities was a priority for the Biden administration on a local and national level, according to a transcript. Biden made several remarks about access to online resources during the town hall. A quick tutorial on giving a BeagleBone Black Internet access from a computer. Despite acting in self-defense, McDonald faced charges of second-degree murder, a common occurrence when Black women seek to protect themselves from violence. In 2012, McDonald received a nearly four-year prison sentence after accepting a plea agreement.
The Dark Web Is A Vibrant Marketplace That Trades In Illicit Goods And Services
Install Avast SecureLine VPN for Android to protect your privacy and keep your data from falling into the wrong hands. The dark net is not quite as lucrative as it used to be and the prices for most of these items or services have gone down in recent years. Great life advice, but it’s even more valuable where the darknet is concerned.
- When Marsha’s Plate discusses violence, they highlight how Black trans women are disproportionately affected in multiple ways.
- Her family is enrolled on the Access program from AT&T but received a one-year-long hotspot as part of a college program.
- These peer-to-peer, invite-only, and/or vouchering networks are faster, cheaper, and less vulnerable to disruption by law enforcement,” Kroll says.
- Data breaches happen all the time, and your login credentials and other data might be on the dark web already.
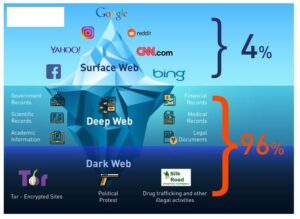
Even one of the best search engines, called Grams, returns results that are repetitive and often irrelevant to the query. Link lists like The Hidden Wiki are another option, but even indices also return a frustrating number of timed-out connections and 404 errors. The terms “deep web” and “dark web” are sometimes used interchangeably, but they are not the same. Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google. Deep web content includes anything behind a paywall or requires sign-in credentials.
The Tor Project says that of the 2 million people using Tor every day, only 1.5% of them are accessing hidden or dark websites (that’s 30,000 people). Most dark web websites are in English; according to one estimate, a staggering 78% of information on the dark web is in English. Many dark internet users favor Tor which uses a network architecture originally developed by the U.S. Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication.

When we asked people about how inconsistent internet access affected their day to day activities, they mentioned going out of their way to obtain it, disrupting their children’s schedules and risking their safety to complete their work online. Miss A is a Black Oakland resident (ZIP code 94612) in her mid 60s, she is completing a professional program and living with a disability that impairs her mobility on very tight monthly income. She uses her phone as a hotspot for emergencies and relies on local libraries to access the internet. She currently studies nonprofit management at Cal State East Bay and is looking for employment.
That may seem an extreme way to browse the web, but such protections are increasingly worth considering, says Sarah Jamie Lewis, executive director of the Open Privacy Research Society. “Some migrate to private forums, other ransomware groups, create new ransomware groups, or adopt decentralized technologies like blockchain-based hosting or intermittent access platforms that are harder to trace and takedown. These peer-to-peer, invite-only, and/or vouchering networks are faster, cheaper, and less vulnerable to disruption by law enforcement,” Kroll says. Despite these limitations, our results have important implications for methods to measure and monitor racism, and to investigate its impact on mortality.
These include crypting services, dropper services, and exploit kits for RaaS and SMaaS, according to Carroll. As dark web operations fragment into smaller, granular communities, cybercriminals are developing their own identities to market their activities and illicit tools. “More than 200 cryptocurrency accounts allegedly owned by the ransomware group were frozen by law enforcement, stripping the group of significant profits,” an AFP spokesperson tells CSO. Continuous monitoring of stealer logs, credential leaks, and dark web chatter should be a core function of threat intelligence, not an occasional sweep after an incident.