It also offers works of art, course material, and audiobooks for download. Following the NYT, the BBC launched a dark web “mirror” of their international edition in 2019. Note that some features of the normal website are not available on the .onion version, including BBC iPlayer.

Facebook’s dark web version allows users to access the site where it is banned or restricted. Although the social application is known for collecting data on its platform, it does not like sharing the information with others. Check out these best onion sites to access the dark web securely and anonymously. Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation. Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. One of the central76 discussion forums was Reddit’s /r/DarkNetMarkets/,777879 which has been the subject of legal investigation, as well as the Tor-based discussion forum, The Hub.
Black Market Products And Services
While some studies have claimed that illegal Bitcoin activity is as high as 44%. Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions. ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users. The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. Content includes non-indexed websites, apps, and resources, which can include protected information such as, online banking, specialized databases, non-linked and password-protected websites, and more.

Discover Content
Weak passwords like the date of your birth, “password 123”, and other easy-breezy ones are a criminal’s dream. Make sure you create strong unique passwords for every online account. Take control of your digital security with an exclusive demo of our powerful threat management platform. The exposed data included customer names, addresses, and purchase details. Shortly after the breach, these records appeared on dark web forums, where they were sold to malicious actors aiming to exploit customers through targeted scams and phishing attacks. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails.
Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. Other sites explicitly block search engines from identifying them. It works by sending internet traffic through volunteer-operated nodes all over the world.
Similar Sites
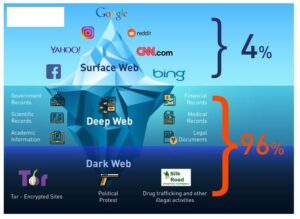
Even platforms like Netflix, which require paid access, are technically part of the Deep Web. You’re only scratching the surface when you use the Internet for daily activities—reading news, managing finances, running businesses. Search engines like Google, Bing, and Yahoo can access just about 4% of the web. The operation extended beyond Spain, with simultaneous searches conducted at several locations in Germany—including Hannover, the Minden-Lübbecke district, and Hessen—as well as in Bucharest, Romania.

Why Was The Silk Road Illegal If The Dark Web Wasn’t?
It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic. The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously.
The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web. In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe. Government cyber teams can take such websites down, arrest the owners and then use the website to track and follow users that show activity on the website. The advantages of I2P are based on a much faster and more reliable network.
Safety Concerns
Black-market evolution mirrors the normal evolution of a free market, with both innovation and growth. Dark web websites are not indexed by standard search engines and can only be accessed using specialized tools, such as the Tor web browser. These sites provide a level of privacy and anonymity unavailable on the surface web, offering content and goods that cannot be easily found through traditional online platforms. For some users — like journalists or whistleblowers — the dark web is about identity protection. It’s where individuals can share anonymous tips with the press on secure drop sites. Special agents like Swensen are looking for the kinds of users who want this full cloak of anonymity in order to mask their illegal activity.
Trusted Directories And Forums (stay Away From Hidden Wiki)
Good starting points are the Onion Directory and the Hidden Wiki. Take a look at the sites that these directories have collected and see what topics interest you. All of these features, its competitive pricing, along with the volume of credit card information listings, make Real and Rare one of the prime sites to trade credit card information online. BidenCash is considered to be one of the most popular credit card sites today and serves as the official sponsor of the popular credit card site Crdpo. Dark web drug sales—which form the majority activity there by volume—represent a small but growing portion of the total worldwide drug trade.

This is an outcome of the ecosystem’s resilience, largely supported by the migration of users15. Correspondingly, the multihoming activity is a mechanism that contributes to the ecosystem’s resilience. To study the performance of sellers, we analyse the quarterly median income, i.e., the quarterly median of the money received by each seller, for each category and multisellers, as shown in Fig. We find that multisellers have the largest median income throughout the period of observation—except in the last quarter of 2017 and 2018, when they have the second largest median income.
- Content includes non-indexed websites, apps, and resources, which can include protected information such as, online banking, specialized databases, non-linked and password-protected websites, and more.
- Third, at any given moment we classify entities as either buyers or sellers.
- Buyers simultaneously active on multiple markets also play the role of connectors in the ecosystem.
- After the original Silk Road collapsed, Silk Road 2.0 quickly rose to take its spot.
Despite Tor’s privacy-focused design, malicious entities are more likely to target your data in transit and on .onion sites. Using Tor to access dark web links isn’t illegal, but your ISP will notice, and others may too. It’s, ironically, more conspicuous than using popular browsers and sites.
Here’s a look at the top 10 dark web markets currently dominating this underground space. Every hour, he sells two to four items chosen at random from a list. He can sell the same item multiple times, on the same rotation, and across multiple rotations.
These cases often involve international law enforcement cooperation and highlight the risks of participating in these markets. Instead of turning to the black market, consider alternative solutions. For example, if you’re looking for affordable medication, explore discount programs or international pharmacies.
After you enter the Harko Village, make your way straight forward through the scanners and the main marketplace. After going a bit further, you’ll arrive at the center of the Harko Village with a big red hologram. After arriving at this location, a cutscene will play that holds narrative importance.