Even the smallest details about you can be useful to cybercriminals. That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform. These hackers don’t hide in the shadows as much as you might think.

This survey highlights active and recently shuttered markets with actionable metrics and intelligence for threat hunters, CISOs, and red team leaders. Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats. After that, many other marketplaces kept trying to take its place and become the top dark web market.
Darknet Threat Actors Are Not Playing Games With The Gaming Industry

Archetyp Market was dismantled in June 2025 during Operation Deep Sentinel in a coordinated raid across six countries. At the time, it had over 600,000 users, 17,000 listings, and approximately €250 million in transactions. Authorities seized €7.8 million and arrested operators in Germany, Spain, Sweden, Romania, the Netherlands, and the US Europol leads takedown of Archetyp. Ethically, they must minimize harm, responsibly handle any stolen or sensitive data (often notifying victims or law enforcement), avoid entrapment, and maintain research integrity.
Norway’s Biggest Drug Bust Happened Online
The site allows users to find and buy a vast variety of products and services. It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity. Of course, not all the popular and widely-used dark web sites and things like marketplaces on the dark net are illegal. Nevertheless, most people on the internet do not need to communicate or venture into the dark web. Imagine an underground version of your favorite online marketplace, somewhere hidden, exclusive, and often operating outside legal boundaries.
How KELA Cyber Supports You In Darknet Monitoring And Risk Mitigation
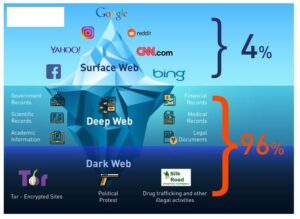
The anonymity and encryption provided in dark markets create a haven for cybercriminals and nation-state actors to buy and sell dangerous assets while evading detection. Dark markets are online platforms on the darknet where illegal goods and services are traded. You can find drugs, weapons, stolen data, and counterfeit documents on these marketplaces. They operate similarly to regular e-commerce sites but use cryptocurrencies for transactions.
- Just like on the regular internet, phishing is a big problem on the dark web as well.
- Regular browsers can’t visit sites with onion addresses, but Tor can.
- Next up is Abacus, another newer market that has already made a massive name for itself, especially following AlphaBay’s closure.
- Chainalysis data shows darknet marketplace revenue dropped post-Hydra seizure in 2022 but recovered to $2 billion in Bitcoin inflows during 2024 Darknet market BTC inflow drop and shift to Monero.
- Most dark markets have user review systems and vendor ratings to establish trust.
Cryptocurrency Transactions
- And in a world where almost everything we do is online, taking your digital privacy seriously is more important than ever.
- Anything from planting malware and stealing sensitive files to hijacking email accounts or breaking into social media profiles.
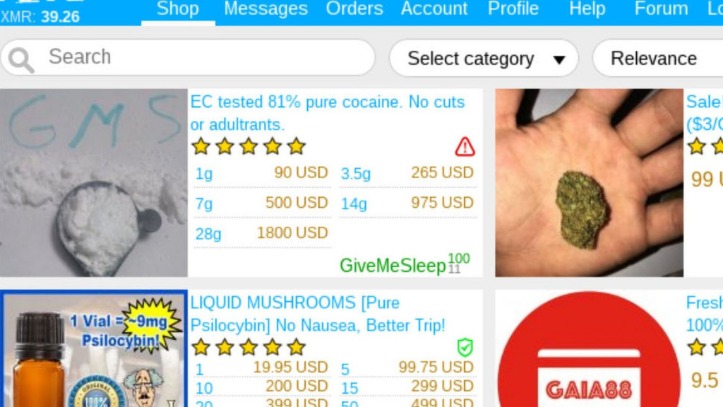
- And when it comes to paying, the site sticks to Bitcoin (BTC) and Monero (XMR) to keep transactions private.
- One thing that distinguishes BidenCash on the dark web, however, is how it markets itself.
- They employ various techniques, such as tracking and infiltrating dark markets, developing advanced threat intelligence, and enhancing international cooperation.
Silk Road quickly grew into the largest darknet market, handling hundreds of millions in transactions. But in 2013, law enforcement traced Bitcoin activity, monitored DPR’s forum posts, and exploited server vulnerabilities to identify Ross Ulbricht. He was arrested in a San Francisco library while logged in as site admin. Darknet marketplaces emerged around 2011, with Silk Road setting the standard for how these platforms operate.
The darknet is used for anonymous communication, accessing censored information, and protecting privacy. Journalists and activists use it to communicate securely in oppressive regimes. You can access it for legitimate purposes like whistleblowing and freedom of expression. However, it’s also used for illegal activities like drug trafficking, weapon sales, and stolen data trading. Law enforcement agencies monitor it for criminal activities, but legitimate users rely on it for privacy protection.

What Is A Darknet Market?
Like ransomware, criminals can buy software and inject your devices with viruses. With it, they can spy on people, steal their sensitive data, or secretly control their devices. These software are also capable of launching DDoS attacks and phishing campaigns. On the dark web, you don’t need to be a technical expert to design ransomware, and that’s dangerous. Even people with little to no knowledge can buy ready-made ransomware and launch attacks on their victims. If for any reason, you decide to visit these hidden corners of the web, ensure you at least study and understand the common traps.

Why Is It Critical To Monitor Dark Web Marketplaces?
The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities. Of course, the promise of secrecy and unfiltered access might lure you in, but those same features are what make the environment so risky. Many people go to the dark web to buy things they can’t find elsewhere, but what if what you’re buying is also trying to harm you? Scammers on darknet markets claim to offer legit tools or services, but instead provide you with malicious software that can infect your device.
The Marketplace As An Arsenal
Understandably, as in the case with most illicit trade markets, you don’t even need to verify your email Awazon. So, what even is this dark web, and why are these marketplaces present there? With the rise of camouflage in technology, the darkweb is going to get more intricate, and marketplaces will become more difficult to spot and take down.

For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy. Whilst a great many products are sold, drugs dominate the numbers of listings, with the drugs including cannabis, MDMA, modafinil,108109110 LSD, cocaine, and designer drugs. If you want more peace of mind, NordVPN has a dark web monitoring tool you can consider using. This handy feature monitors the dark web for signs that your login details or other personal info have been leaked. However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere. For instance, after the closure of Genesis Market, its website came back after a few weeks.
Darknets FAQs
So, if a “business opportunity” sounds too perfect, it probably is. Once many users begin to rely on the site and store funds in escrow, the operators disappear, taking all the money with them and leaving their customers and clients with nothing. Drug dealers can sell to customers across the world, not just locally. This expanded reach, combined with anonymity, only makes it easier for them to grow their operations without getting caught immediately. Attempting to interpret the clock face as part of a captcha is a simple mistake that can be easily avoided.
Tracking vendor migration—such as from Archetyp to Exodus—provides insight into tactical shifts. Focusing intelligence collection on specialised marketplaces yields better ROI for threat detection and proactive defence. In 2025, darknet marketplaces primarily accept Monero (XMR) and Bitcoin (BTC). Privacy-focused operators are shifting to Monero due to its default anonymity, compared to Bitcoin’s transparent ledger Darknet markets see BTC inflow drop to $2B. Darknet marketplaces remain central to illicit trade in 2025, with evolving business models, payment systems, and law enforcement responses.