
“If the user chose to open the file, a video file containing images of child pornography began to play, and the FLA captured and recorded the IP address of the user accessing the file,” the FBI complaint reads. Some of the related court documents were recently shared by a user on Reddit. Thomas Peter Katsampes, 52, of Eagan, Minnesota, pleaded guilty to conspiracy to advertise and conspiracy to distribute child pornography on Feb. 27. Those arrested locally recently include Joshua DeWitte, a former music teacher at Buckingham Browne & Nichols School in Cambridge, and Christopher Allan Tisoy of Baltimore. They were charged in federal court in Boston with sexual exploitation of children. DeWitte, who is already facing related state charges, is accused of sending payments totaling nearly $24,000 to Tisoy to produce videos of boys being sexually exploited in the Philippines.
Parents Kill 4 Children In Dominican Republic Amid Spate Of Such Murders
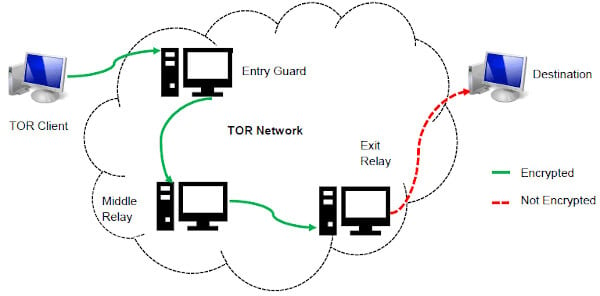
The dark web hosts a wide range of sites — from whistleblower tools and secure email platforms to underground forums, black markets, and dark web mirrors of legitimate news outlets. Exploring the dark web can be eye-opening, but it’s also risky without the right protection. While the Tor browser boosts privacy, pairing it with a VPN adds a critical layer of security. On the dark web, traffic is routed through multiple server nodes that don’t log activity, obscuring the user’s origin and enabling anonymous communication.
… But Federal Funding Has Remained Almost Flat
Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies. This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. Formerly known as Archive.is, it is one of the best onion sites on the dark web. While this is not much compared to standard email services, it is enough for PGP-encrypted messages. You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web.
Tips included tutorials on how to encrypt and share material without being detected by the authorities. The anonymity offered by the sites emboldens members to post images of very young children being sexually abused, and in increasingly extreme and violent forms. “People who traffic in child exploitation materials are on the cutting edge of technology,” said Susan Hennessey, a former lawyer at the National Security Agency who researches cybersecurity at the Brookings Institution. With so many reports of the abuse coming their way, law enforcement agencies across the country said they were often besieged.
Playpen had three administrators, including Fluckiger and Chase, and numerous moderators, including Browning, according to court documents. Admins handled the technical aspects of the site and hosted it, developed and enforced rules, and other tasks. Moderators, meanwhile, didn’t have such a technologically hands-on role, and kept the forum clean and organised. However, it is not clear from the court documents what exactly constituted a seizure of the second child pornography site. The documents don’t say whether this refers to the FLA running the site from their own servers, similar to the Playpen case, or whether it took control of a primary administration account and allowed the site to continue operating.
That said, anonymity comes with a dark side since criminals and malicious hackers also prefer to operate in the shadows. For example, cyberattacks and trafficking are activities that the participants know will be incriminating. The use of the dark web usually means that you are attempting to engage in activity that you could not otherwise carry out in the public eye. The dark web refers to sites that are not indexed and only accessible via specialized web browsers. Significantly smaller than the tiny surface web, the dark web is considered a part of the deep web. Using our ocean and iceberg visual, the dark web would be the bottom tip of the submerged iceberg.
What Is Tails Software Used For?
But users should always be cautious and avoid clicking unfamiliar or untrusted links to steer clear of scams or malware. The dark web is a hidden part of the internet not indexed by regular search engines, accessed through specialized browsers like Tor. It hosts both legal and illegal activities, offering anonymity but also posing risks like scams and illicit content. In Shouse’s role, he “maintained the website which allowed users to post links to images and videos of CSAM,” the Justice Department said.
A Dark Web Child Porn Site Is Forcing Its Visitors To Learn Security Tips
For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed.
Epping Asylum Hotel Timeline As Government Secures Court Victory
Others may act in ways that are illegal for the protection and safety of others. Let’s unpack both of these concepts in terms of the “dark web browser” and the websites themselves. As such, the dark web has attracted many parties who would otherwise be endangered by revealing their identities online. Abuse and persecution victims, whistleblowers, and political dissidents have been frequent users of these hidden sites. But of course, these benefits can be easily extended to those that want to act outside of the constraints of laws in other explicitly illegal ways.
Even though DuckDuckGo is the Tor browser’s default search engine, it doesn’t index dark web websites, which means you won’t be able to find .onion sites with it. SecureDrop is an anonymous file-sharing platform designed for secure communication between whistleblowers and journalists. While anyone can use it, it’s built for high-stakes exchanges, making it overkill for routine file sharing or data backups.
Hot On Social

The U.S. Federal Bureau of Investigation (FBI) arrested Ulbricht in October 2013, but imitators still arise, many much larger. So far, authorities have arrested 79 individuals linked to Kidflix, while more than 1,400 suspects have been identified. Among those detained were not only consumers of the illegal content but also direct perpetrators of abuse. First, download the Tor browser, which will give you access to dark web sites and keep you anonymous while searching the sometimes-seedier corners of the internet. The dark web was created, then, for people interested in surfing the internet anonymously, and the sites within the dark web often cater to illegal activity.
- The deep web rests below the surface and accounts for approximately 90% of all websites.
- The deep web is basically all the content that you can’t find using Google or Yahoo search.
- Onion links have no regular domain names registered under the domain name registry.
- Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe.
- The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose.
- It encrypts your traffic at the entry node and changes your IP address.
Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Unlike other search engines, it does not collect or share web activities and personal data of users. When viewed through this lens, the dark web’s legality is based on how you as a user engage with it. You might fall to the wayside of legal lines for many reasons that are important for the protection of freedom.

Mr. Davis, who was sentenced to 30 years in prison in 2016, said that “capturing the abuse on video was part of the excitement,” according to court records. “The predominant sound is the child screaming and crying,” according to a federal agent quoted in the documents. The fallout for law enforcement, in some instances, has been crushing. McIntosh, shackled in orange prison garb, scanned the empty seats reserved for his family as deputies led him from the courtroom.
Legitimate Use Cases For The Average User
But while anonymous email services can help protect your identity, they don’t make you immune to threats like email spoofing or social engineering. And it’s still essential to use strong passwords and two-factor authentication (2FA) to help keep your account secure. This list is not exhaustive, and there are many more types of onion sites on the dark net, including websites offering fraud services, botnet panels, file repositories for pirated media, forums for extremist groups, and more.

The release of Freenet in 2000 is considered by many as the start or founding of the dark web. University of Edinburgh student Ian Clarke created Freenet as a thesis project. Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones.



