
Hence, every word has 2 vectors, each describing the word’s relations with other words in one corpus. In the meantime, these 2 vectors are still comparable because they are used together in the neural network to train a single skip-gram model for predicting the surrounding windows of context words. Laws pertaining to anonymity and the use of privacy-enhancing tools vary widely from one country to another.
What’s The Difference Between The Deep Web, Dark Web, And Tor?
Law enforcers can use custom software to infiltrate the dark web and analyze activities. You could be monitored closely even if you are not doing anything illegal. Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography.
The Shift Toward Smaller, More Niche Markets
Notably, the 2023 Index also reveals a ‘strong and statistically significant’ correlation between the synthetic drugs trade and cyber-dependent crimes. According to the Index, the online purchasing of synthetic drugs may suggest the existence of an established cyber environment, which implies a heightened risk of cyber-dependent criminality. Torch is one of the oldest dark web search engines, and it’s generally considered one of the safest. It has some advertisements on its home page, but they’re for popular searches and services to help get you started. However, make sure you’re careful which links you click on — some of them lead to sites that contain illegal content and services.
Popular Things You Can Purchase From The Dark Web Marketplaces
If you need a great Tor VPN, I recommend ExpressVPN — all its servers allow Tor traffic, it has excellent security and privacy features, and it provides fast browsing speeds. OnionName lets you generate an .onion domain name that starts with a specific keyword — like onionamev33r7w4zckyttobq3vrt725iuyr6xessihxifhxrhupixqad.onion/, which is OnionName’s dark web link. The keyword in that example is “onioname,” which is right at the start of the .onion link. With a readable site name like that, people will know what to expect when they click on the link. SecureDrop protects your privacy by encrypting your data, which makes it unreadable.
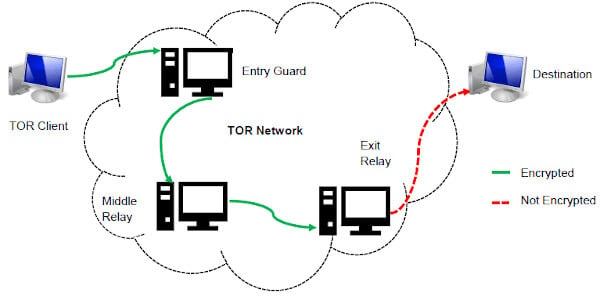
Best Anonymous Dark Web Browsers On The Tor Network
All of this underscores Riseup’s prioritization of users’ rights over business interests. ProPublica is independent, so you’ll find trustworthy news reports on topics ranging from corruption to inequality and environmental issues. As a bonus, the site is one of the most polished on the deep web, so you shouldn’t get a clunky experience that feels sus. Not to be confused with the riskier Hidden Wiki page, Wikipedia on Tor serves as a vast repository of information. You’ll find articles on a wide range of topics, such as history, science, and culture — and that’s just scratching the surface. So take this guide as you explore where to go on the Tor Browser without risking your online security.
ProPublica — Investigative Journalism On Tor
The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy. ProPublica is a non-profit, Pulitzer Prize-winning news outlet that focuses on abuses of power and issues of public trust. ProPublica’s investigative journalism can upset powerful interests, so the outlet joined the dark web to help their journalists and readers access their content anonymously. Being on the dark web also lets whistleblowers send material to ProPublica without fear of reprisal. To be clear, I don’t nor do I want to sell drugs, personally I don’t see the risk being worth the potential profit.
How Do I Find onion Links For Sites?
Darknet market lists play a crucial role in simplifying access to these platforms. By aggregating verified links and providing up-to-date information, these lists reduce the time users spend searching for reliable markets. They also include user reviews and ratings, helping newcomers identify trustworthy vendors and avoid scams. As the demand for darknet drug trade grows, these markets are expected to continue improving their infrastructure, offering users even greater levels of privacy and efficiency. The combination of technological advancements and user-centric features positions these platforms as the leading choices for secure and reliable drug trade in 2025. These markets also prioritize user feedback and reviews, allowing buyers to make informed decisions based on the experiences of others.
Subscribe To The Blog Newsletter

Some respondents said that being protected from physical risk on the dark web is not only a benefit for existing drug suppliers, but may also make the activity attractive to people who would not otherwise be willing to sell drugs. This January, the FBI was part of another international operation that took down the cybercrime marketplaces known as “Cracked” and “Nulled”. According to DOJ, Cracked and Nulled provided access to “stolen login credentials”; personal “identification documents”; and “hacking tools”– impacting at least 17 million victims in the U.S. “During Operation SaboTor, our law enforcement partners spoke with over 100 Darknet drug buyers. He says gaining access to those darkest sites on the platform is not easy. The sellers are wary of being infiltrated by law enforcement, so don’t let just anyone in.
- These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies.
- The absence of dosage regulation means a single pill can contain lethal amounts, increasing the likelihood of fatal overdose.
- Over the next decade, piecemeal studies began to reveal a notable portion of drug sales were being mediated by social platforms.
- Because of the escrow, the sellers or the buyers can not scam each other.
Silk Road And Early Markets

Onion sites (aka Tor sites) are websites only accessible on the dark web; you can’t view them using a regular browser. Their URLs (aka dark web links) have .onion as the domain, instead of the common surface web domains like .com or .net. I wanna provide labelled products, good advice and service, like a real business. Not sit in a shitty car park selling $10 bags from a car window all day.
The market is especially well-known for providing access to freshly compromised data, often obtained from recent breaches and stealer logs. This platform has rapidly become a key player in the fraud market, trading in PII and SSH credentials while making use of both the clear and dark web. The platform is favored by cybercriminals seeking access to accounts that can be exploited for fraud or sold to others.
It’s used by 50+ news organizations, including ABC, Bloomberg News, CBC, and The New York Times. It doesn’t censor out any content, so you’ll have free access to more than 400,000 indexed pages. I like that you can ask the search engine to match all of your search words for exact results, or only some of them for broader search results. Get the latest in privacy news, tips, tricks, and security guides to level-up your digital security. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. Keybase is an exciting identity service that aims to make it easy for you to link the presence of your online identities together in a cryptographic way.
Buyers, often facing long transplant waiting lists, turn to unregulated channels in search of life-saving procedures. Sellers may be coerced by financial hardship, misled by false promises, or trafficked against their will. The absence of medical oversight raises concerns about surgical safety, post-operative care, and long-term health outcomes for both donors and recipients.
However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. Surfshark supports unlimited simultaneous connections to protect as many devices as possible. Also, try its services risk-free with the 30-day money-back guarantee. This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session.



