Carefully matching your needs to the strengths and weaknesses of each solution ensures optimal privacy, security, and usability. It offers outstanding privacy features and there is currently a discounted rate available through this link. In combination with that data, and data gathered by other methods and/or tactics may in fact lead to complete exposure and could eventually lead to the police standing at your doorstep. You can either sell or buy goods on the dark web, but both present difficulties. In opennet mode, the network will automatically assign you to other users on Freenet’s network.
How Do I Find onion Websites Safely?

This setup is easy to configure, and you don’t need any special settings or features. Just turn on your VPN, wait for the connection to stabilize, and launch Tor. Your internet activity is still subject to exit node risks, so always use HTTPS and avoid entering any personal information on unencrypted sites. Even with Tor and a VPN, you’re not fully protected unless you also lock down your behavior. Most dark web leaks happen when users skip basic safety steps or reveal too much without realizing it. Use the tips below to patch common blind spots and avoid easy-to-make mistakes.
Introducing The Risk Dashboard: Cyberint’s Answer To The Challenge Of Measuring & Mitigating Cyber Risk

Avoid clicking unverified links from results, and cross-check with directories to prevent phishing. This setup ensures anonymity while leveraging NotEvil’s privacy-centric, no-log design. To safely access NotEvil, first download Tor Browser from the official site and connect via a reputable VPN like NordVPN for added IP masking. It’s beginner-friendly with simple keyword searches and no registration required, making it easier to explore privacy tools or forums without overwhelming clutter. By 2029, engines may support DID-based access to gated .onion communities, streamlining research while preserving privacy. NotEvil’s community-driven ethos aligns with this trend, though adoption hinges on user trust and technical maturity.
- These digital currencies are shielded by advanced encryption technologies, facilitating anonymous, seamless transactions without reliance on a central authority.
- Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions.
- Additionally, ensure that the VPN service has a wide network of servers in various locations to offer you more options for server locations.
- Tor over VPN and VPN over Tor both involve using a VPN with the Tor network, but in different orders.
- Users will need to navigate this divide, favoring open-source tools for transparency.
Step 2: Install Required Software On Ubuntu
Additionally, if Tor leaks, your IP address will be exposed to everyone. You can eliminate these privacy concerns by connecting to a VPN before launching the Tor Browser in a setup called Tor over VPN. For most people, Tor over VPN is the safer and more practical choice. It protects your real IP address even if Tor leaks, is easier to set up, and works with most major VPN services.
Mobile Optimization And Accessibility
You’ve probably heard that Tor makes you anonymous on the dark web — but that’s only half true. If you don’t use the right tools or settings, your ISP can still flag your connection. And once you’re inside, one wrong click on a fake .onion site can expose your identity or infect your device with malware.
Which Is The Best Laptop For Cyber Security Course?
Download) or I2P (Invisible Internet Project). While these networks ensure user traffic is anonymized and generate addresses for hosting dark web sites usually ending in “. Relays help route traffic securely by passing encrypted data through multiple nodes before reaching its destination.
✅ Legal Content
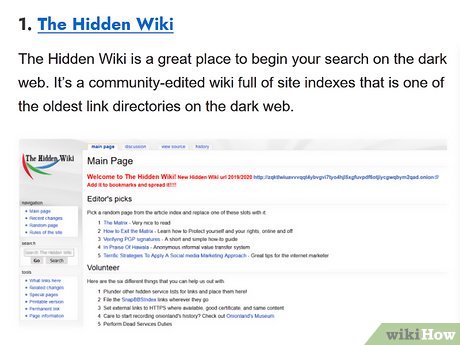
- In 2025, I revisited The Hidden Wiki to locate a SecureDrop instance for a whistleblower story.
- NotEvil’s inclusion enhances the guide’s value, offering a privacy-centric, ad-free engine that bridges Ahmia’s safety and Torch’s scope.
- In this article, we will delve into the Dark Web and provide a step-by-step guide on how to explore and make purchases within its marketplaces.
- A VM can act as a protective barrier between your main device and any potential threats.
- Typically, any reference to the visible web will be to common websites with a familiar internet domain extension.
- This process, though, can often involve accessing the dark web for research into the most current malware on the market.
Early detection through consistent surveillance of dark-web channels allows companies to respond swiftly, minimizing harm and protecting organizational integrity. Lastly, staying informed and continuously assessing and upgrading your security measures is vital. Remain vigilant, adapt to evolving risks, and be mindful of any changes in regulations or best practices. Is due to the ever-evolving nature of the dark web — search engines there simply can’t keep up with the changes, often providing irrelevant or repetitive results. The US military created the dark web to protect US intelligence communications online.
Can I Use Tor Browser Without Installing It?
Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation. It uses its own internal DNS to access “eepsites”, not .onion addresses. Tor protects your identity inside its network, but it doesn’t hide everything. Your ISP still knows you’re using Tor, and entry nodes can see your real IP address.
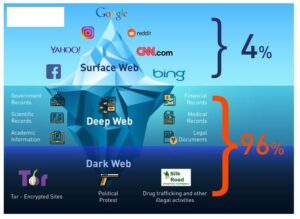
The dark web is the third layer of the internet and the hardest to find. It consists of websites that use the “.onion” top-level domain instead of “.com”, “.net”, etc. You can’t access “.onion” sites through regular browsers like Chrome and Firefox. Accessing the dark web requires special tools and precautions, like using the Tor browser. However, the Tor network can be hacked, as evidenced by the 7 months of DDOS attacks experienced in 2022 (Securityaffairs)1. There are files available on the dark web, which may harbor hidden malware.
Its focus on V3 .onion addresses aligned with Tor’s security upgrades, but its unfiltered results required robust user caution. Torch’s launch around 2010 marked the first true dark web search engine, indexing millions of .onion pages with a keyword-based system. Torch’s massive, unfiltered index enabled broad exploration, but its spam-heavy results and lack of safety measures reflected the dark web’s Wild West ethos. Users relied on handwritten lists or email chains to share .onion links, with no centralized indexing. The lack of search tools made the dark web a fragmented, insider-driven space, inaccessible to most. I’ve used it to jumpstart research, like a 2024 privacy guide that needed reliable .onion links fast.
Social engineering tactics are also common, where bad actors try to get you to willingly give up sensitive information, like login details, financial information, etc. To avoid encountering disturbing or illegal situations, I advise against entering darknet sites before thoroughly researching them. I also recommend that you browse the dark web with complete anonymity by using a VPN — just to be safe. Accessing the dark web on mobile devices comes with greater security risks compared to using a desktop. You can access the dark web on both Android and iOS, but their limitations make it less secure.
Where Can I Find Safe Onion Links?
Underground marketplaces, known as darknet markets, provide a platform for exchanging illicit goods and services, including drugs, weapons, counterfeit documents, and stolen data. These marketplaces operate using cryptocurrencies like Bitcoin to ensure anonymity in financial transactions. Without a VPN, the first server in the Tor network (the entry node) can see your real IP address, and your internet service provider (ISP) can see that you’re accessing the dark web. This creates a privacy risk even if they can’t see what you’re doing on the dark web. Plus, in some regions, accessing the dark web alone may raise suspicion or get you flagged for extra monitoring.
Install Tor Browser from the official website, adjust security settings to “Safer” or “Safest,” and only use trusted onion links from verified directories. Understanding the Dark Web and its access tools, such as Tor, is crucial for anyone considering exploring these hidden parts of the internet safely and responsibly. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access. These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties. Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites. From this point onwards, you can enjoy complete anonymity and security while being able to access “.onion” websites and other dark web browser domains.
Make sure you download the Browser from the official website (torproject.org). Downloading and installing the Tor Browser should only take you 2–3 minutes. As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. As such, you should exercise caution when accessing any unofficial dark websites. Like I2P, Freenet is a self-contained network within the network that can’t be used to access sites on the public web.
Malicious exit nodes can monitor your traffic, and browser fingerprinting can track you. Governments also often monitor Tor usage, even if they can’t see your activity. It’s recommended to take safety precautions when accessing the dark web, even if you’re after legitimate content. You cannot access the dark web using regular browsers like Chrome, Edge, or Safari. You must use a secure web browser that prioritizes privacy and security and can access onion sites.