Monitoring for data breaches, using identity theft protection, and implementing multi-factor authentication can reduce the risks if your data ends up for sale. Sites like AlphaBay (now defunct) or Hydra have hosted sprawling markets selling everything from stolen credit card details and personal identities to malware and hacking tutorials. Would-be insider traders are also given the tools to get the job done. In some cases, administrators provide users with malware samples so insiders in the financial industry can quickly gather the information they want without any need for specialized knowledge. According to the forum’s creator, there are members of the club which make more than $5,000 a month by trading leaked data such as stolen credit cards. Insider trading on the dark web is a serious problem that can have severe consequences for those involved.
Dark Web Marketplaces: The Trade Of Illicit Goods And Its Impact On Cybersecurity For Businesses
- However, at the end of the day, you just never know who you are talking to on the Dark Web, and that thought alone should have given Jones pause.
- Any statements about profits or income, expressed or implied, do not represent a guarantee.
- Other general statistics about our dataset can be found in the Section S3.
- Tor (Onion Routing), the most popular and practical anonymous communication system, is a common way for individuals to access the dark web.
- Whether you’re considering the allure of anonymity or the promise of exclusive assets, tread carefully in the world of Dark Web crypto trading.
- The first operation took place in 2018 and successfully led to the arrest of 35 sellers41, while the largest operation to date occurred in 2020 and led to 179 arrests in six different countries42.
It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. The only difference is that it passes your traffic through random nodes before reaching the destination.
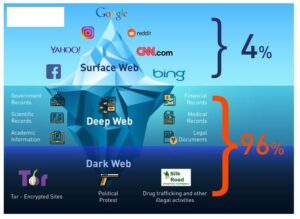
Types Of Dark Web Sites (and What Really Goes On There)

The largest component of the S2S network of U2U transactions between sellers for each year with the respective number of nodes (N). The nodes are sellers that are active in that year, and an edge is placed between two sellers if at least one transaction occurs between them during that year. The network is mostly populated by U2U-only sellers, followed by market-only sellers. After a major external shock in 2017, the S2S network shrinks but, unlike the multiseller network, recovers, and grows again (though slower than the multibuyer network). The largest component of the S2S network one year before and one year after the operation Bayonet.
US And Five Global Partners Release First Unified OT Security Taxonomy

In this article, we will explore the phenomenon of insider trading on the dark web. In order to investigate the role of direct transactions between market participants, we now analyse the evolution of the S2S network, i.e., the network of the U2U transactions involving only sellers. The nodes of the S2S network are active sellers (i.e., sellers that are trading at the time) and two sellers are connected by an edge if at least one transaction was made between them during the considered snapshot period. Although the S2S network is composed only of U2U transactions, all categories of sellers (i.e, market-only, U2U-only, and market-U2U) are present in the S2S network. For instance, market-only sellers are entities classified as sellers only in markets, but that may promote U2U transactions with other sellers, hence being part of the S2S network.
Ready To Explore Web Data At Scale?
Whether local or international goods, research documents, banned drugs, you name it, everything is available on this dark web platform (that’s one of the reasons why this should be monitored for security purposes). Unlike other search engines, it does not collect or share web activities and personal data of users. Introducing Abacus Market—the premier dark web marketplace for 2025. Featuring over 75,000 listings and a network of vetted vendors, it’s built for confidentiality and security.
🛡️ How Axis Intelligence Strengthens Cybersecurity
From drug sales and breached data to scam services and malware, dark web markets are some of the most dangerous corners of the internet. These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in illegal goods and criminal services. Although individuals may anonymize activities, researchers are already exploring ways to exploit security vulnerabilities to infiltrate, de-anonymize, and track malicious behavior.
This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy. The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world.

Inside Meta’s Insider Trading Controversies

You will find all the necessary .onion links to access any content or service on the dark web. Tor hosts thousands of message boards where all posts are anonymous. This totally anonymous setting makes the proliferation of sensitive information very easy and safe for the users. Since there is a loser on the end of every insider trade, your money and retirement could be at risk.
Avoid trusting anonymous sources on the dark web who claim to have insider information or insider trading tips on the dark web. Anonymous sources are often unreliable and may be attempting to scam you. There have been several cases in recent years of individuals engaging in insider trading on the dark web. One example is the case of Ukrainian hacker Oleksandr Ieremenko, who allegedly stole confidential information from the US Securities and Exchange Commission (SEC) and used it to make trades. Another example is the case of the former Equifax CIO Jun Ying, who used insider information obtained through his employment to make trades and avoid significant losses.
Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. The Tor browser gives employees a marketplace to exchange insider information on their firms for Bitcoin or insider information on other public firms.
Other options include Ahmia and NotEvil, which focus on listing .onion links. Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. Formerly known as Archive.is, it is one of the best onion sites on the dark web. It aims to preserve the internet’s scientific and cultural heritage. While this is not much compared to standard email services, it is enough for PGP-encrypted messages.
Drugs, Drugs And More Drugs: Crypto On The Dark Web
By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. This variability is driven by the pattern of informed and uninformed traders selecting where they trade, but only when market conditions are normal. In other words, it holds when volatility is moderate and the spread between the ask and bid prices on the exchange is narrow. Under these conditions, uninformed traders gravitate towards the dark pool because they face lower risk of adverse selection there.