Here you can learn the key differences between Deep Web vs Dark Web vs Shadow Web and what each of these terms refers to. If you want to access the Dark Web, follow the security measures pointed out in this blog to be safe and anonymous while reaching out. Deep and Dark Web are two different concepts, but easy to understand.
The Difference Between Deep Web And Dark Web, In Short:
Privacy and security work differently in each one, and it’s important to know what to expect. In other words, the Deep Web is everything you use daily but isn’t open to the public. When asked about the deepweb, he looked a bit taken aback by the question. Being a smart guy, he quickly responded saying that the deepweb is simply another name for the darkweb. As I pondered over the discussion, I realized that there is definitely a grey area in the IT community when it comes to the difference between surface, deep, and darkweb. This prompted me to share my views on the topography of the internet that we all know and use today.
Similarities And Differences
Sure, neither can be search-indexed, but large sections of the the Deep Web, unlike the darknets that form the so-called Dark Web, do not need any special censor-resistant software for access. The Dark Web, on the other hand, can only be accessed through various anonymizing platforms, the best-known and most widely-used among which happens to be Tor. Other platforms like I2P and Freenet are also generally referred to as being parts of the Dark Web. It turns out that a majority of cybercriminals, selling everything from compromised personal and financial data to drugs and hacking tools, constitute over half of Dark Web contents.
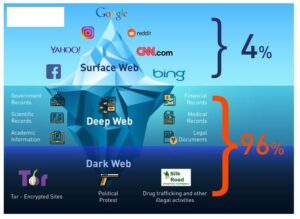
Generally, when we search for anything, we get thousands of articles, videos, and images, which gives us the impression that the surface web is massive. However, there are estimates that this could be just 4-5 % (even less by some estimates) of the entire web. The remaining 95 % (or more) is made up of information that is not indexed. The part which is not indexed cannot be accessed using our regular search engines. Due to limited accessibility, we are generally unaware of the relative scale of the deepweb and darkweb in comparison to the surface web. To understand the difference further, let us go over the basics of how internet search engines work.
The differences between the Deep Web and the Dark Web have implications for law enforcement. Agencies are increasingly concentrating on monitoring Dark Web activities due to the rise in cybercrime and illegal trade, attempting to enact appropriate measures to protect general society. Next, select a dark web search engine like DuckDuckGo that can help you find dark web websites that cannot be indexed by traditional surface web search engines, such as Google or Bing. Standard search engines index these websites and are accessible without special configuration. The good news is that there is a much faster version of privacy technology that is similar to Tor, albeit much faster. A VPN is a technology that (like Tor) provides you with a string layer of encryption to stop local networks, ISPs, and government agencies from being able to monitor your online activities.
How To Use The Dark Web Safely?
- A study by researchers at King’s College London that examined the contents of over 2,700 darknet sites found that approximately 60% of them hosted illicit content.
- An early version of the Tor browser was created to combat the challenges presented by the lack of privacy during the initial days of the internet.
- As previously mentioned, more than 90% of the traffic on the internet is already on the deep web, so the keys to accessing it safely are virtually the same as the keys to accessing the open web safely.
- Law enforcement officials can also set up traps to capture criminals engaged in illegal transactions.
- Domain addresses on the dark web typically use non-standard top-level domains like “.onion” instead of common extensions like “.com” or “.org,” making them inaccessible through conventional browsers.
- You’ll find everything from your email inbox to private databases and paywalled content here.
The dark web is a small, hidden subset of the deep web that requires special tools to access. The dark web is home to all sorts of illicit activities and is considered unsafe. As mentioned earlier, regular browsers cannot access dark web websites. The dark web uses “The Onion Router” hidden service protocol to function. Tor servers are used for surfing; they are undetectable from search engines and offer users complete anonymity. The Dark Web is designed to provide privacy and anonymity to its users by encrypting and anonymizing the traffic by using darknets.

How CrowdStrike Protects You From Illegal Dark Web Activity
His writing typically combines his expertise in software, technology, business, and finance. The dark web is the smallest part of the internet ecosystem—even smaller than the surface web. It only hosts a few thousand sites, accounting for just 0.01% of the entire internet. The dark web’s infrastructure serves those needing privacy, including activists, whistleblowers, political dissidents, and even regular citizens attempting to escape censorship or persecution.
Conclusion: Navigating The Digital Landscape Safely
Darknets and Dark Web sites are encrypted, peer-to-peer networks that are only accessible via certain tools. Most Dark Web users use the TOR browser, which is designed to make the Dark Web easier to navigate. The TOR browser provides improved privacy and anonymity on the public Internet and makes it possible to access .onion sites on the Dark Web. “The Dark Web” is an overused term that can be a source of mystery and confusion for most cybersecurity professionals.
Building A Smart Security Pipeline
However, if you’re determined to access the dark web, there are several steps you should take to protect yourself. Pay close attention to the data permissions you authorize, which means you don’t want to click “yes” each time a popup appears on a website asking for it. However, even if you follow these tips, ultimately, some info regarding you will appear on sale on the dark web. Fortunately, if this data is no longer accurate to create harm, you have little to worry about – especially if you use multi-factor authentication. Additionally, using robust anti-malware software is another way of staying safe. It is encrypted and regularly updated, meaning your data won’t be easily accessible to malicious parties.

By combining proactive monitoring, secure infrastructure, and tools like SAGA®, organizations transform confusion into clarity. Properly managed, the dark web becomes less a risk and more a source of strategic insight—supporting resilient, informed decision-making. The threat intelligence team uses this insight to reset passwords and launch an internal investigation. The Dark Web refers specifically to websites and services hosted inside Darknets. Search engines do not index these sites and use domains like .onion (for Tor) or .i2p (for I2P).
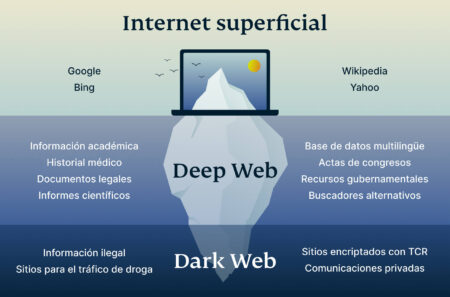
This includes personal email accounts, online banking portals, cloud storage, subscription services, and medical records — essentially, any page behind a login, paywall, or restricted access. The “deep web” (also called invisible and hidden web) refers to the 90% of the internet information that is not accessible to the general public because it is not indexed by search engines. The contents of the deep web can be accessed by using a direct URL or IP address along with user account credentials. The “dark web” is a specific portion of the 90% of the deep web that requires specific technologies to access due to it existing on an overlay network of the internet commonly referred to as the Darknet. The deep web contains all parts of the internet that aren’t indexed by standard search engines like Google or Bing.
Let’s look at some of the most commonly asked questions and myths surrounding this subject. Remember, whether you’re diving into the depths of the deep web or cautiously exploring the dark web, always prioritize your security and ethical considerations. These three terms are often a source of confusion, especially in connection with cybercrime and where that comes from. There’s also an increased chance of downloading malware, leaking credentials due to a phishing scam, or falling victim to financial fraud due to the lack of oversight. Accessing the Deep Web generally involves fewer risks compared to the Dark Web, but there are still some considerations.
What’s The Difference Between The Deep Web And The Dark Web?
Finally, law enforcement agencies can access the dark web to detect illegal activity, such as weapon deals, drug distribution, and financial crimes. For instance, money laundering can be detected by correlating cryptocurrency wallet addresses with illicit activities. Law enforcement officials can also set up traps to capture criminals engaged in illegal transactions. The former includes privately protected file collections that one cannot access without the correct credentials. The latter includes internal networks for governments, educational facilities, and corporations. The ‘members only’ parts of public platforms are also a part of the deep web.
At the top, there is the “visible or surface web.” The visible web is what you’re looking at right now. Because Google bots and other web crawlers index them, you can find these pages with a quick online search. While the deep web serves a largely communal and educational purpose, the dark web often invites danger, fraud, and crime. Each layer of the internet requires users to approach their activities with mindfulness, adopting necessary precautions to protect themselves against potential threats. In an increasingly digital world, the internet has become an essential element of our daily lives. We rely on it for communication, shopping, learning, and entertainment.