In that case, there is a high chance that your data will become accessible to cybercriminals. Then, they can use your data to impersonate you and run social engineering attacks to target your loved ones. However, with the right security measures and cautious browsing, you can minimize these dangers. As dark web websites are not moderated, they can host a wide range of malware, such as ransomware, keylogger, and remote access Trojan. You can inadvertently download malicious software by visiting these websites, infecting your system.
Best Onion Sites By Category
Organizations of all sizes should consider dark web monitoring so that if any sensitive data is ever leaked onto the dark web, you can take quick action. Quite often, a detected dark web leak of user login credentials is an early warning sign that a cyberattack might be imminent. While it started as a hidden network for controversial content, whistleblowers, and gambling, the dark web has become a more dangerous and widespread black market.
Terrorist Content

The term dark web first appeared in print in a 2009 newspaper article describing these criminal applications. Riseup is a volunteer-run social movement organization that offers email, email lists, a VPN, online chat, and other online services for political activists engaged in various causes. Riseup’s services can be accessed on the surface web or via Tor websites if users want to protect their anonymity. It’s legal to use the dark web in most countries, but there are places where using the dark web might be against the law. I strongly advise doing your own research to make sure you’re not breaking any local laws by visiting the dark web. Also, even in countries where accessing the dark web is legal, it’s still against the law to use or host sites that promote criminal activities.
Don’t Stick Your Nose Where It Doesn’t Belong

They asked for our personal information in exchange for access to the forum. We didn’t give them any information, but it’s scary to think how legitimate they sounded in the email. In the same vein, online scams are much more prevalent on the dark web than on the surface web. Scammers are bolder and much more daring because they know they’re untraceable.
Can A VPN Boost Your Internet Speed? Here’s
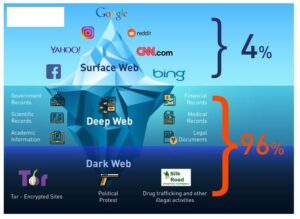
- While the deep web comprises about 90% of the total web, the dark web makes up just a tiny fraction of the deep web total.
- Scientific journals often put their articles behind a paywall and charge high fees for access, but Sci-Hub offers open access to read or download research papers.
- With a particular interest in privacy, data, and security, Rosalyn has covered social media, AI, IoT, deepfakes, marketing tech, the cloud, enterprise tech, consumer tech, and digital transformation.
- Keep reading for a rundown of the best dark links you might want to check out.
- Each relay decrypts a layer of encryption to reveal the next relay in the circuit and passes the remaining encrypted data on.
The site is strongly resistant to hackers and encrypts your data in transit as well as the rest. Among many open-source whistleblower sites, SecureDrop is currently a leading platform. Many prominent media sources and journalists maintain a presence on this website location to securely accept documents from anonymous senders. These include big names, such as Al Jazeera, CBC, Forbes, Huffington Post, The New York Times, and many more.
The Rise And Fall Of Ransomware: Insights From Avast’s Q1/2023 Threat Report
There are multiple search engines on the dark web that can help you find what you’re looking for. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content. The deep web is made up of content that search engines such as Google do not index. Such data includes medical records, financial information, research papers, private forums and networks, and other content.
DigDeeper offers in-depth analysis of technology and privacy topics rarely covered by mainstream media. The website’s articles focus on digital rights, surveillance, and security research. I found their technical explanations clear and well-researched, though the site updates less frequently than other news platforms. Cybersecurity risk assessments and regular monitoring of dark web activities are essential to identifying and mitigating threats before they result in significant damage.
Visiting the dark web, if you don’t exercise caution and have enough security, poses many security and legal risks that can lead to data theft, identity fraud, and legal consequences. The dark web also offers access to blocked resources in countries with strict government censorship on the internet. Citizens of such countries can use the dark web to bypass firewalls and access global information.
- Still, for those willing to put up with the inconvenience, the dark web provides a memorable glimpse at the seamy underbelly of the human experience – without the risk of skulking around in a dark alley.
- The use of the dark web raises suspicion as it shows there is something you want to do privately.
- However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it.
- The network is comprised of thousands of volunteer-run servers known as Tor relays.
Onionname
But navigating the dark web is full of cybersecurity and legal challenges. A large portion of activities on the dark web involve illegal content, transactions, or services. Simply accessing certain sites or engaging with the wrong links could implicate you in criminal investigations. The dark web hosts various types of illegal content, such as stolen data, child exploitation material, and prohibited items. As an average Internet user, you may accidentally stumble upon such content.
DuckDuckGo — A Dark Web Search Engine

The dark web works over the internet, but instead of having your traffic routed from your computer and through the normal network of servers, it stays within the Tor network. You won’t know exactly what system you’re accessing unless they tell you, and they won’t know who you are unless you tell them — or unless one of you is careless. UpGuard can protect your business from data breaches, identify all of your data leaks, and help you continuously monitor the security posture of all your vendors. It cannot and does not attempt to protect against monitoring traffic at the boundaries of the Tor network (traffic entering and exiting). Onion routing encrypts data, including the next node destination IP address multiple times by sending it through a virtual circuit of successive, randomly selected relays. This had led to some services restricting functionality to Tor users.
Ratings are easily manipulated, and even sellers with long track records have been known to suddenly disappear with their customers’ crypto-coins, only to set up shop later under a different alias. Experience Flare for yourself and see why Flare is used by organization’s including federal law enforcement, Fortune 50, financial institutions, and software startups. By monitoring and analyzing dark web activities, organizations can gain actionable insights to stay ahead of cyber threats. They can sell access to compromised systems, trade in stolen credentials, and much more. Being able to tap into these conversations, transactions, and threat actor behaviors equips businesses with valuable intelligence to fortify their defense systems.
If you need to access dark web resources, these are the steps you need to take. Here’s everything you need to know about this other internet, as well as how to access it. The area of the internet we access daily is known as the clear or surface web.
Forums And Communities
Although the social application is known for collecting data on its platform, it does not like sharing the information with others. It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web. The dark web relies on encryption protocols and specialized software like Tor to anonymize user activity. Tor routes data through multiple volunteer-operated servers, or “nodes,” disguising the original IP address and location. This multi-layered encryption gives the network its “onion” structure, and each layer makes it more difficult to trace back to the source.
The blog contains tons of useful guides about how you can avoid online surveillance. SecureDrop protects your privacy by encrypting your data, which makes it unreadable. Also, it doesn’t log your IP address or any information about your browser or device. Moreoever, the servers are owned by the organizations that use the service. The best news is Torch updates its sites every single day, so you’ll always be able to browse the latest news and access new services and sites.
The darknet version of DuckDuckGo is not a search engine for the dark web, but a private browsing tool for the dark web. DuckDuckGo’s regular site can take you to the dark web, as it brings up onion sites and dark web links when searched. Neither DuckDuckGo’s dark nor normal versions keep a log of your web activity. The best dark web websites provide access to educational materials, host secure services, or bypass censorship. Dark web websites are hidden under layers of encryption that cloak user activity, which can be a boon to whistleblowers, activists, and others who don’t want anyone tracking their activity. DuckDuckGo is a search engine available on the Tor network that lets you browse the surface and dark web.