Its inherent anonymity allows everyone from dissidents to whistle-blowers the opportunity to share information free from persecution. In many cases, this information can itself be used to prevent illegal activities. Sophisticated tracking technologies, compromised entry nodes, or poorly managed anonymity practices can lead to user identification and monitoring by governments, hackers, or other entities. The dark web hosts numerous sites explicitly designed to distribute malware. Viruses, spyware, ransomware, and other harmful software can compromise your device, steal sensitive data, or enable remote spying. The dark web remains one of the internet’s most intriguing yet misunderstood environments.
VPN Alternatives For Securing Remote Network Access
It allows you to buy and sell a wide range of products and services with a good user experience. This site supports PGP encryption and two-factor authentication features. However, in April 2022, this site went offline after American and German federal government law enforcement agencies seized the website servers. Some alternative links are available, providing access to the marketplace. It’s recommended not to use new alternative links as they could just be planned exit scams.

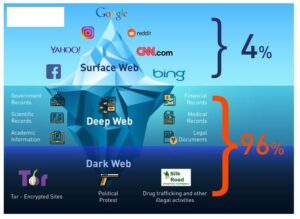
Not to mention that anonymity safeguards won’t protect you from other threats like hacking and malware. There are media websites on the dark web—both legitimate and illegitimate—that allow users to access digital media outside the highly monitored surface web. As you might expect, these websites sometimes host explicit, gory, harmful, and illegal content. Dark web marketplaces are websites where you can exchange illicit goods and services like stolen credit cards, account login credentials, counterfeit items, drugs, and other items.
Step 3: Connect To The Tor Network
In a way, it feels more like a private club than an open market, and that’s exactly how the operators want it. The tool can of course also be used to surf the internet anonymously without criminal intent. To do this, click on “Connect” in the “Connect to Tor” dialogue.
How To Use The Resetter Adjustment Program Epson L15150 And Save Service Costs
Dark net websites are called “Tor hidden services”, and they can be distinguished from normal websites by their URLs. Later, Tor’s underlying code was released under a free license, and a nonprofit called the Tor Project was formed. In 2008, the Tor Browser was released, which made it easy for anyone to get on the darknet. The existence of an anonymous and hidden internet then allowed for alternative information channels and illegal websites to flourish. In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network.
Are Sites On The Dark Web Illegal To Use And Visit?
The Invisible Internet Project (I2P) Browser emphasizes a fully encrypted, decentralized approach to dark web access, routing traffic through an anonymous network of user-operated tunnels. It supports both web browsing and secure communication, offering additional services like email and instant messaging fully integrated into its secure environment. It is also advisable to be aware of the credibility and security of the sites visited and to be cautious about disclosing personal information. The Mega Darknet hosts a wide range of activities, both legal and illegal. Legitimate uses include the protection of privacy and the free exchange of information in countries with strong censorship or surveillance.

The hidden nature of the dark web has earned it the nicknames black web and underground internet. However, these names likely conjure up a scarier conception than the real definition of the dark web. Have you ever downloaded a file on your iPhone and then struggled to find it later? Streaming devices have become the backbone of digital entertainment in homes and offices. Opt for curated sources like Dark.Fail (PGP-verified mirrors) and Ahmia (filters abuse). Treat Hidden Wiki with caution and verify any link via multiple sources.
Ready To Explore Web Data At Scale?
This means you can go on the darknet privately while downloading torrents on the side. There are numerous phishing sites, too, as explained earlier, designed to fool users into giving up their personal data. Many cybersecurity and tech experts recommend using a VPN whenever you want to access the dark web via the Tor Browser or any other specialist browser.
It also has inbuilt productivity tools such as a processor and an email client, which means once you’ve got TAILS installed, you can do much more than just browse the web safely. When accessing the dark web, the last thing you want is to leave traces behind that could be traced to you. Setting up the Tor and VPN separately is recommended if this is a concern. If you want privacy and anonymity, NordVPN accepts payment in Bitcoin. Moreover, it offers a 24/7 customer support service and a 30-day money-back guarantee.
How Many Onion Sites Are There?
There are some websites you can absolutely get in legal trouble for even visiting, so proceed with the utmost caution. In this guide, we’ll show you what you need to know about how to access the dark web and how to keep yourself safe while you use it. It will normally take a while to connect because Tor — unlike other browsers — will route your traffic through different nodes. You should also keep in mind that overall speeds will likely be impacted; for example, a page might take a few seconds longer to load than what you are used to. The Tor network is operated by thousands of volunteers worldwide who maintain the proxy servers that protect your identity.
Method II – VPN Over Tor
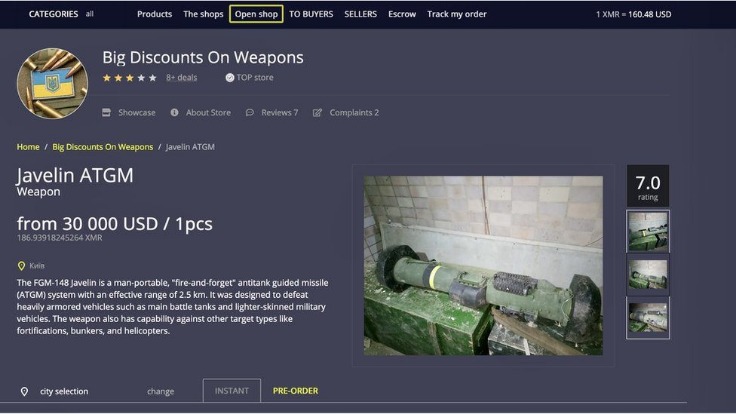
But what’s important for freedom of information in countries with strong censorship naturally also attracts many criminals. The darknet and its marketplaces not only offer drugs, medicines, doping agents, online identities, credit card data, and false passports, but also weapons of all kinds. The dark web and the deep web are often used interchangeably, but they’re two distinct concepts. Founded by security researcher Juha Nurmi, Ahmia is essentially a list of “hidden” sites that do want to be found. Onion sites are “crawled” and added to the list provided their “robots.txt” file permits it, and if it is not on their blacklist of sites with abuse material.
Are There Any Torzon Mirror Events Or Workshops?
It works by first using a VPN and connecting to Tor afterward, hence its name. If you don’t know where to start, you can use The Hidden Wiki to find a few dark web domains. Simply copy the URL of the site you want to visit, press Enter, and you’re all set. You might’ve heard of the domain extension called “.onion“, which sits at the end of each dark web website. Indeed, these websites use “atypical” names and domains to present themselves. So, instead of “facebook.com”, the URL can look like “12ls834mfdg8.onion”.
- Simply download the file, install the software, and you’re ready to use its web-based interface.
- The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you.
- Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content.
- Step into the world of Archetyp, where anonymity reigns supreme.
- The Hidden Wiki is a directory hosted on the clear net (also called the “surface web”) that contains a list of .onion links for many of the best dark web websites.
As a matter of fact, your data could be anywhere on the internet, meaning it could already be at the three internet levels (surface web, deep web, and dark web). If you live in the EU and want to know what data your provider has collected about you, the GDPR gives you the right to request a full report. However, it is often prohibited for ISPs to sell your data to third parties. With all this data, your ISP could create a very accurate profile of you and link it to your IP address. This is one of the reasons why it is always good to hide your IP address. Sometimes, they even know more than you would like about private matters, such as your health or finances.
Can You Be Traced On Tor?
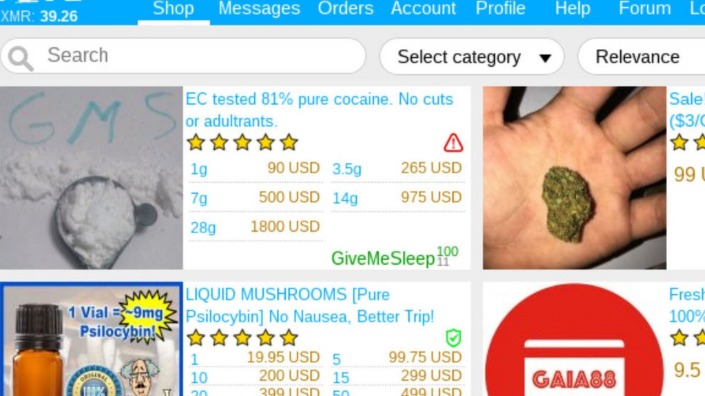
These marketplaces are full of risks (security, legal, ethical issues – all of them). But if you still decide to access these websites, for education or research purposes, make sure you stay cautious. Naturally, this makes the dark web a breeding ground for illegal activity. But onion sites can also serve nobler goals, like providing access to information and independent journalism in countries with government censorship.
The darknet is a mysterious and often misunderstood part of the internet, attracting both intrigue and concern. Darknet markets, in particular, have gained attention for their role in facilitating the exchange of illicit goods and services. Despite their controversial nature, these marketplaces continue to evolve, offering a glimpse into the darker side of online commerce. As cyber threat intelligence professionals monitor these markets, they gain insights into emerging threats and malicious activities that can impact organizations and individuals.