Want to get illegal drugs, fake passports, Trojan, or other cyber attack software? Plus, there’s a thorough vetting process for new buyers and sellers to keep the community more secure. In a way, it feels more like a private club than an open market, and that’s exactly how the operators want it.
Best Free Firewall Software In 2025
In this article, we’re going to explore a hand-picked list of the 18 books that deliver unique, helpful, and thought-provoking insights into the dark web. Dark web books aren’t just how-to guides for breaking the law or dodging surveillance. (Forget what you think you know.) Instead, they offer a peek into the minds of the people who actually navigate this hidden digital realm and explore the real-world impact it has on our society. Several books today offer insights into the dark web, which is unknown to many.
Staying anonymous requires continuous learning, self-awareness and legal caution. Tor is supported by US government, many NGOs, private foundations, research institutions, private companies and over 20,000 personal donations from people from around the World. It’s a modified Firefox that allows access to the dark web and is configured for higher security. However, the TOR browser can and is used to do regular browsing by people around the world.
Why Use The Tor Browser With A VPN
Moreover, sensitive personal documents are made available on the dark web. Some things, like medical records, driver’s licenses, and passport information. The consequences can be lethal to those whose data is stolen, like identity theft, emotional distress, and even financial loss. Perhaps, hiring a hacker can feel impossible, but it’s a genuine threat that you need to be aware of.
Community Forums
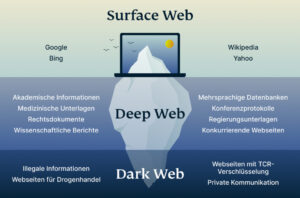
Usually dark web transactions are made with Bitcoin or other cryptocurrencies. There are numerous directories that host .onion links and websites, but you should always exercise caution. This portion of the internet can be accessed using search engines such as Google, Bing, or Yahoo. It includes websites, databases, and other online resources indexed by search engines and is easily discoverable by users. The open web makes up less than 5% of the internet, which is just the tip of the iceberg of the entire internet.
These websites will also use .onion top-level domain names, and many of them will be very long, random combinations of letters and numbers. You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers. VPNs are also used for accessing geo-locked content hosted by streaming services.

Did The Silk Road Marketplace Go Under?
- You can even find things such as BIN checkers and PayPal cookie converters.
- As long as users take the necessary precautions, no one knows who anyone else is in the real world.
- With all this data, your ISP could create a very accurate profile of you and link it to your IP address.
- You can use the VPN rated #1 for the dark web with no restrictions for a month—great if you want to try this no-log provider’s Onion over VPN servers for yourself.
- You may also use it to access the regular internet more anonymously.
The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. The dark web — aka, the deep web — is the second layer of the internet, which is not indexed by search engines. Websites and pages in the deep web might include password-protected content, private forums, and personalized resources.

Security Blogs
Simply download the file, install the software, and you’re ready to use its web-based interface. In opennet mode, the network will automatically assign you to other users on Freenet’s network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others.
What Are Darknet Markets?
First, in the USA, it is a federal offense to use the USPS for any of these transactions. If the buyer or seller gets caught, there are significant legal ramifications. Note that loading sites with TOR usually takes considerably longer than on the clearnet.
Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. The Darknet is often utilized for secure communication, discreet information or file sharing, anonymous research without identity exposure, and occasionally for engaging in illicit activities. It is also recognized for hosting underground black markets(darknet markets), whistleblowing platforms, and discussion boards that champion freedom of speech.
Darknet Marketplaces are underground black markets on the dark web! Shop for exclusive products in our marketplace, where privacy, security, and anonymity are always a top priority. Abacus hosts over 250+ active vendors offering a wide range of products, including drugs, digital goods, fraud tools, and counterfeit items. Step into the world of Archetyp, where anonymity reigns supreme. Archetyp Market is an online darknet marketplace, founded in late 2021. At present, MGM Grand is the host of over 23,000 listings that are categorized into Fraud, Drugs, Digital Goods, Guides & Tutorials, and Miscellaneous.

When engaging in online activities over Tor, refrain from providing identifying information, including your name, email address, or financial details. Create new handles or pseudonyms to protect your identity throughout your online engagements. By the late 2010s, a myriad of platforms allowed users not just illegal goods but also forums for activism, whistleblowing, and even genuine speech that found little outlet in conventional media.

Do I Need A VPN To Access The Dark Web?
The significance here lies in the potential damage to individuals and businesses. Companies must implement strong data security measures, employ encryption, and monitor for data breaches to protect customer and employee information. Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy. This encryption ensures that messages cannot be intercepted and read by third parties, including law enforcement. The use of digital signatures can also help verify the authenticity of users and transactions. Dark markets, as well as various other services within darknets, are hosted as ‘hidden services’.