Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world. And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. Well, there’s a reason why it’s recommended to browse with a minimized or rescaled window – you can be tracked based on your active window’s dimensions (yeah, they really can do that).
How Do Onion Routing And Tor Work?
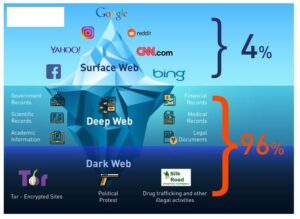
If you need to access dark web resources, these are the steps you need to take. The dark web, however, requires special software to access, as explained below. Here’s everything you need to know about this other internet, as well as how to access it. The area of the internet we access daily is known as the clear or surface web. The internet opened the door to a realm of possibilities that permanently changed the business landscape and our personal lives.
MULTI-LAYERED ENCRYPTION
- It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee.
- The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines.
- This reality has led to an ongoing debate about whether the dark web should exist.
- However, if you’re communicating with state intelligence agencies, you should use Tor alongside a VPN for maximum privacy.
- Indeed, most nations; including the United States, the United Kingdom, and India, allow access to the dark web as a lawful activity.
- It has a vast library of over 1.5 billion indexed pages that lets you find whatever you are looking for.
|
- If you are still unable to connect to the onion service after verifying the address, please try again later.
- ActiveX and Java frameworks are susceptible to being exploited by hackers.
- For real-time messaging, Ricochet Refresh offers decentralized, peer-to-peer encrypted chats over Tor without central servers, greatly reducing surveillance risks.
- Using a VPN, like Forest VPN, adds an additional layer of security by encrypting your data and masking your IP address.
- For instance, always use strong passwords that mix letters and symbols, making them hard to guess.
|
- The CIA (Central Intelligence Agency) provides a .onion version of its website, enabling individuals to bypass restrictions to access its content from anywhere.
- Go to the directory where you saved the downloaded Tor Browser installation file.
- This setting forces all website connections to use the secure HTTPS protocol rather than HTTP, an insecure version that leaves you vulnerable to eavesdropping.
- TorlanD opens up access to a vast range of hidden content, allowing you to navigate the deep web freely without restrictions.
- That’s why we always recommend using a VPN over Tor—even if you feel you have nothing to hide.
- We have never received a compensation in any form for operating this website.
}
Husain is also a part of the vpnMentor Cybersecurity News bulletin and loves covering the latest events in cyberspace and data privacy. By following these precautions, you can explore the dark web with a greater degree of safety and security. Onion links are URLs that end with .onion and can only be accessed through the Tor network. While not mandatory, using a VPN adds an extra layer of privacy and security by hiding Tor usage from your internet service provider.

To maximize security, you should avoid logging into personal accounts, such as Facebook and Gmail, via Tor. Although the Tor Browser is designed with strict privacy, logging into personal accounts can expose your real identity. The tradeoff is that you don’t get personalized search results, as DuckDuckGo doesn’t collect user data. But this tradeoff is worthwhile when seeking to browse with the utmost privacy.
What Is The Onion Network?

Because of its anonymity, the dark web is filled with illegal services and is used by numerous criminal groups, including ransomware gangs. It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Through the dark web, users in places of high censorship can also access information and news. To make its journalism more accessible to readers around the world, the New York Times launched its onion service in 2017.
Shuttered Dark Web Marketplaces
But it also contains other news and religious sites, private discussion forums, and medical records. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web. In addition, the content on the pages don’t need any special or custom configuration to access.
How To Safely Access The Best Dark Web Sites – Quick Guide
While the Tor Browser does an excellent job of protecting your privacy and anonymity, you really shouldn’t use it as your daily driver browser. Go to the directory where you downloaded the Tor Browser installation file. Right-click on the downloaded file and select “Extract Here.” Once the Tor Browser setup files have been extracted, double-click on “Tor Browser Setup” to install the browser. Go to the directory where you saved the downloaded Tor Browser installation file. Choose your language and click “OK.” Follow the installation prompts. There are four nodes between your computer and the website you want to connect to.
How To Get Started With Tor Browser – A Web Browser Designed For Privacy
Unlike many dark web platforms, it maintains strict content guidelines while protecting user privacy. These sites are intentionally hidden to protect the privacy and anonymity of both the site operators and visitors. Haystack is a dark web search engine designed with privacy in mind, similar to Duck Duck Go. The problem is, the dark web isn’t indexed by regular search engines. Contributing a relay helps make the Tor network faster, more robust against attacks, more stable in case of outages, and protects the anonymity of its users.
The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. This article lists some of the best dark web websites you can visit securely. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article). Though people usually think of dark websites as the wrong online place, that’s not the complete truth.
Use Active Monitoring Of Financial And Identity Theft
Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. While this is not much compared to standard email services, it is enough for PGP-encrypted messages.
To access a dark web resource, you will need to know its web address to the letter. These websites will also use .onion top-level domain names, and many of them will be very long, random combinations of letters and numbers. You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers. When you try to visit a website on a normal web browser (like Google Chrome or Firefox), your web traffic goes through several routers on the internet before it reaches its destination. In short, you don’t have anonymity – this lets hackers, your ISP (Internet Service Provider), or companies like Facebook snoop on what sites you visit. As hoped, the Tor anonymous network grew in popularity among computer enthusiasts, privacy advocates, journalists, dissidents under repressive governments, and others desirous of strict secrecy.
- Chainalysis says that $790 million worth of cryptocurrencies were used to shop in darknet markets during 2019.
- While there are numerous VPN services that work well with Tor, I’ve found that NordVPN offers the best protection and compatibility, and keeps your personal information safe.
- There are other ways for spies, hackers or other adversaries to target Tor.
- The process costs a fee, but unlike other “tumbler” or “mixing” services, there is no risk that Wasabi or any of its users could scam you out of your coins.
You need to ensure you’re only accessing reliable dark web sites, and the ones listed below are among the safest ones that currently work. This repository contains a comprehensive list of .onion links to various resources available on the dark web. The links are organized into categories such as general resources, marketplaces, and email services. This collection aims to provide users with a broad overview of available dark web resources. When you access an onion site, your connection is first routed through a series of these nodes, which are randomly selected. This not only anonymizes your IP address but also encrypts your data multiple times.
Consider Using A VPN (Virtual Private Network)
I especially like how TorLinks categorizes links based on their type, letting you easily find what you need. As a result, the dark web has become a breeding ground for illicit activities because government agencies face significant challenges in identifying the operators behind hidden services. The core functionality of the dark web relies on onion routing, a method that encrypts and routes user communications across multiple servers, known as nodes.
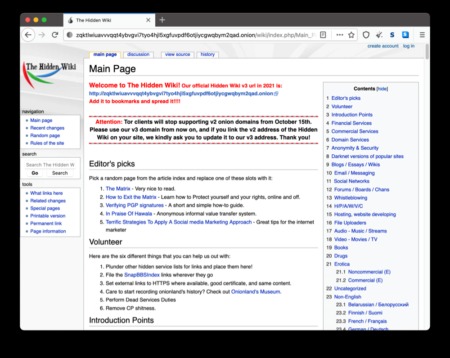
Search engines and corporate websites might be OK, but even a popular Tor website like Hidden Wiki can show illegal deep web links that jeopardize your online safety. Dark web websites are pages that exist on a part of the internet that isn’t indexed by traditional search engines like Google. Also known as deep web sites, these pages typically have URLs ending in .onion and are only accessible through special software like the Tor Browser. These trusted sites will help you gain confidence and minimize risks.