Its inherent anonymity allows everyone from dissidents to whistle-blowers the opportunity to share information free from persecution....
access
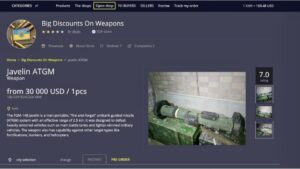
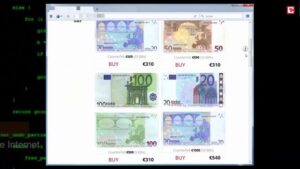
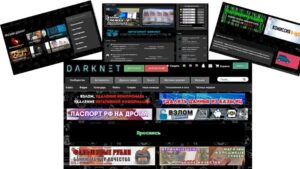
There are a variety of illegal markets, and all of them work in different ways. A black...
Your data is encrypted in the Tor browser before reaching the ZeroBin servers. Formerly known as Archive.is,...
It can only interact with the gateway, the most effective method by which the browser protects user...
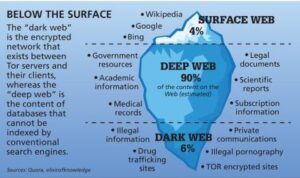
It encompasses public domains such as websites, social media platforms, news sites, and online stores—content accessible to...
They offer various electronic services, including physical technology, Internet services, entertainment programs, communications plans, etc. Deep web...
It has been estimated that a large percentage of dark web traffic is related to illegal pornography...
Markets like Incognito even nudge you to use it for extra peace of mind. Over the years,...
ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted...
Also, enable automatic connection to the VPN whenever you use the internet, including when accessing the Dark...